SMA Publications
NSI maintains an extensive Publications archive of government-sponsored research and analysis products, various research efforts from our professional and technical staff, and a variety of corporate news items. The government-sponsored products are maintained on behalf of the US Department of Defense (DOD) Strategic Multilayer Assessment (SMA) program and address challenging national security problems and operational imperatives.

Foreign Approaches to Gray Zone Conflicts.
Author | Editor: National Intelligence Council.
The purposeful application of multiple elements of power—information, economic, military, political—to achieve objectives in ways that exceed the threshold for normal competition yet fall below the level of major interstate war.
“Gray Zone cannot mean everything if it is to mean anything.” “Gray Zone” conflicts are not synonymous with “Hybrid War.” “irregular War” or “MOOTW.” Intent, not the means, primarily distinguishes “Gray Zone” conflicts from other types of conflict. Why conduct “Gray Zone” conflicts? To avoid major power war and costly penalties, hinder an effective response by intentionally blurring peacetime and wartime operations, and control Escalation.
Question (Follow-up QL3): The response to QL5 (see Appendix A) noted that ISIL is moving to ZeroNet platform for peer-to-peer messaging, which is extremely robust to distributed denial-of-service (DDOS) attack/other counter measures. What effect could this have on Intel efforts?
Author | Editor: Robinson, S., Perez, E., Derrick, D. & Ligon, G. (University of Nebraska, Omaha).
Through our research into Da’esh cyber messaging (Derrick et al., in press), we have identified an emerging trend in Da’esh forum, propaganda, and fundraising websites: the use of the ZeroNet application. ZeroNet, a peer-to-peer application, uses the same technology as Bitcoin or other cryptocurrencies using shapeshift.io. As Da’esh users begin publishing their websites off servers using this ZeroNet application, visitors are then only able to visit that website (e.g., blogs, chat forums) using that ZeroNet application. This facilitates/mandates that visitors then seed that content to other viewers, as the website is distributed to and from many locations and from multiple small servers. When the website is updated, the update is pushed out to all seeders. Each website visited is also served/seeded by the visitors, thus creating a distributed publishing system that permeates more than just one physical site owner.
Implications
The use of this application is another instance of Da’esh as an early adopter of IT Innovation (Ligon, Derrick, Logan, Fuller, Church, Perez, & Robinson, 2016). ZeroNet is built for hosting all types of dynamic websites, and any type of file can be distributed on it (e.g., VCS repositories, databases, etc). Creating ZeroNet websites is facile and instructions can be located on a variety of open source websites1 and easily installed. Implications we have identified are 1) DDOS is no longer an option for technical interdiction unless all seed accounts can be hit at one time, 2) taking down a website that violates user terms (e.g., suspicious content, hate speech) is no longer an option, 3) social engineering will play a larger role to gain access to protected sites, and 4) cyber interdiction may need to focus on heavier preventative measures rather than post hoc take-downs/removal. However, one positive implication is that Blue could also use the seeding to find supporters of Da’esh in the following ways. First, by seeding real or other content, analysts can become part of the network that hosts these websites. This can allow them to monitor who seeds the content to identify other potential supporters. However, this technique is limited if the other seeders use an anonymizer, such as an anonymous VPN or tor. The ability to find other seeders will often (not always) be limited to the organizations ability to analyze the tor network. Finally, as with other Da’esh endorsed applications (e.g., Dawn of Glad Tidings, monitoring who downloads the ZeroNet application in months following its 1 Websites such as https://zeronet.readthedocs.io/en/latest/faq/ walk users through the pros and cons of ZeroNet and are available in at least 22 languages. Endorsement on Da’esh communication channels (circa October 2016 and weeks following, one could track IP addresses for those who do not use TOR to mask their identity (this instruction was not included on the initial post about downloading ZeroNet . Second, because the content is secured in same manner as bitcoin wallet, bitcoin hacking and identification techniques would also be effective on this application. Finally, an innovative way to take down content is to infiltrate creator accounts and make updates with blank content to disrupt files of seed accounts.
Conclusions
Our assessment indicates that site destruction of user content employing ZeroNet will be more difficult due to its crowdsourced, distributed platform. However, collection of data may in fact be easier. Moreover, using the techniques we recommended and others developed to harvest data from bitcoin users, it may in fact be easier to identify other seeders and downloaders than it has been from 2014-present.
Question (R2 Special): What are indicators of change in Russian strategic interests in Syria?
Author | Editor: Astorino-Coutois, A. (NSI, Inc).
This paper found that Russia¹s strategic interests in the Middle East are fairly stable. What could change is how Russia prioritizes its interests in the wake of the US election and change in administration. Indicators of change might include troop movement or alteration in leader discourse.
Russia’s strategic interests in Syria are fairly stable
Timothy Thomas, a Russia expert from the Foreign Military Studies Office and former US Army Foreign Area Officer (FAO) believes that a fair articulation of Russia’s long-term strategic interests is right where they should be: in the country’s 2015 National Security Strategy (NSS).1 The only “changes” that Thomas expects will be the result of the “gradual accomplishment” of several interests. First among these is strengthening Russian national defense, which in Syria has meant Russian forces taking the opportunity to test new weapons systems and command procedures while working to keep ISIL and Islamic extremists from Russia’s southern borders. Second, Thomas reports that “consolidating the Russian Federation’s status as a leading world power” in a multipolar international system has been accomplished by Russian actions in Syria and Ukraine “in the eyes of many nations.”
What could change? How Russia prioritizes its interests
Thomas points to optimistic versus pessimistic Russian views on how the recent US election will impact US policy in Syria. Optimistically, some feel that the election of Donald Trump may diminish the US security threat, offer Russia new opportunities in the region, and thus allow Russia to prioritize other interests than it has been. This logic is based in the belief that the new US Administration will be willing to tolerate Assad in order to work in concert with Russia to defeat terrorist threat from ISIL and other groups. Russians taking a more pessimistic view however argue that forging a US-Russia partnership in the region will not be as simple as a change of Administration.
What might signal a change?
Dr. Patricia Degennaro (Threat Tec, LLCI -TRADOC G27) believes that “the key to understanding signals for change include Russian rhetoric and key troop maneuvers. The Russian President’s messaging is the signal to change.” Dr. Larry Kuznar (Indiana-Purdue; NSI) reports empirical analysis of President Putin’s language use and whether Putin’s language patterns might be used as indicators of Russian change of strategy in Syria. Dr. Kuznar uncovers a “blip” then “brag” pattern in Putin’s public discourse that may be used as an indicator. Specifically, Kuznar finds that prior to a major event (like invading Ukraine) Putin begins mentioning a few key emotional themes (e.g., pride, protection, unity, strength and Russian superiority) and political themes (e.g., Russian security, Russia’s adversaries, Russian energy), a “blip,” then goes silent presumably during the planning and execution phase. Once the activity or goal is complete however, Kuznar finds that “Putin is characteristically tight-lipped about his interests and intentions, but tends to brag after he achieves a victory.” He habitually “relaxes his restraint and releases a rhetorical flourish of concerns and emotional language”, i.e., some major bragging.
In short, Dr. Kuznar (Indiana-Purdue) finds an empirical basis to suggest that specific linguistic themes such as pride, Russian superiority and France2) as well as more general emotional and political themes “may serve as early indicators and warnings of Putin’s intent.” Currently Putin’s mention of pragmatic themes in relation to Russian energy resources and his recent concern with Turkey, and emotive themes, such as the threat of Nazism, may serve as indicators of his activities if his past patterns are retained. And as such, “may have direct implications for his intentions in Syria.”
Contributing Authors
Kuznar, L. (NSI & Indian University – Purdue University, Fort Wayne), Thomas, T. (Foreign Military Studies Office, US Army), (TRADOC), Degennaro, T. (Threat Tec, LLCI – TRADOC G27)

Speaker: Brig Gen (Sel) Rob Spalding (Joint Staff)
Date: June 2016
Brig Gen (Sel) Rob Spalding is the Chief, China, Mongolia, Taiwan Division, Deputy Directorate for Politico-Military Affairs – Asia, Strategic Plans and Policy Directorate, Joint Staff, the Pentagon, Washington, D.C. As Division Chief, he directs activities and operations to develop planning guidance for Unified Commanders, prepares Joint Staff/DoD positions on National Security Council matters, and develops informal and formal briefings dealing with major national and international policy matters for use by the Chairman, Joint Chiefs of Staff.
Brig Gen (Sel) Spalding received his commission through Fresno State University’s Reserve Officer Training Corps program in 1991. He is an Air Force Command Pilot with more than 2,300 hours flight time in two major weapons systems; B-2 Spirit and B-52 Stratofortress. His prior tours include Command of the 509th Operations Group where he launched B-2s in support of Operation Odyssey Dawn, and Military Assistant to the Deputy Assistant Secretary of Defense for Prisoner of War/Missing Personnel Affairs at the Pentagon. During the Iraq surge in 2007, he deployed and directed the Personal Security Coordination Center, and was responsible for security of the top five leaders in Iraq.
Prior to his current assignment, he was the Air Force Military Fellow at the Council on Foreign Relations, New York, NY. Brig Gen (Sel) Spalding speaks Chinese-Mandarin and Spanish.
EDUCATION
- 1987 Bachelor of Science degree in agricultural business, Fresno State University, CA.
- 1993 Master of Science degree in agricultural business, Fresno State University, CA.
- 1998 Marine Corps University Amphibious Warfare Course (Correspondence).
- 1999 Squadron Officer School (Distinguished Graduate), Maxwell AFB, AL.
- 2001 Defense Language Institute Chinese-Mandarin Course (Distinguished Graduate), Monterey, CA.
- 2003 Air Command and Staff College (Correspondence).
- 2006 Air War College (Correspondence).
- 2007 Joint Forces Staff College, Norfolk, Va.
- 2007 PhD economics and mathematics, University of Missouri, Kansas City, MO.
- 2008 Air War College, Maxwell AFB, AL.
- 2008 Masters of Science degree in strategic studies, Air University, Maxwell AFB, AL.
- 2013 Graduate Certificate, Nuclear Weapons Effects, Policy & Proliferation, Air Force Institute of Technology (AFIT), Wright-Patterson AFB, OH.
ASSIGNMENTS
- 03/1992 – 08/1993, Officer in Charge, Strategic Plans, 21st Space Wing, Peterson AFB, CO.
- 08/1993 – 09/1994, Student Pilot, 87th Flying Training Squadron, Laughlin AFB, TX.
- 11/1994 – 05/1995, B-52 Upgrade Training, 11th Bomb Squadron, Barksdale AFB, LA
- 06/1995 – 05/1998, B-52 Pilot and Aircraft Commander, 23rd Bomb Squadron, Minot AFB, ND.
- 05/1998 – 05/2001, T-38 and B-2 Pilot, Wing Life Support Officer, Conventional Strike Officer, and Chief of Training, 325th Bomb Squadron, Whiteman AFB, MO.
- 06/2001 – 06/2002, Chinese-Mandarin Student, Defense Language Institute, Monterey, CA.
- 07/2002 – 04/2004, Olmsted Scholar, Tongji University, Shanghai, PRC.
- 04/2004 – 06/2006, B-2 Instructor/Evaluator Pilot and Assistant Director of Operations, 393rd
Bomb Squadron, Whiteman AFB, MO. - 06/2006 – 07/2007, Military Assistant to the Deputy Assistant Secretary of Defense, Defense Prisoner of War/Missing Personnel Affairs Office, Pentagon, Washington, DC.
- 08/2007 – 01/2008, Director, Personal Security Coordination Center, MNF-I, Baghdad, Iraq.
- 01/2008 – 06/2008, Deputy Director Strategic Plans and Initiatives Directorate, Defense Prisoner of War/Missing Personnel Affairs Office, Pentagon, Washington, DC.
- 07/2008 – 06/2009, Student, Air War College, Maxwell AFB, AL.
- 06/2009 – 06/2010, Chief of Safety, 509th Bomb Wing, Whiteman AFB, MO.
- 06/2010 – 03/2011, Deputy Commander, 509th Operations Group, Whiteman AFB, MO.
- 03/2011 – 04/2012, Commander, 509th Operations Group, Whiteman AFB, MO.
- 04/2012 – 06/2013, Vice Commander 509th Bomb Wing, Whiteman AFB, MO.
- 07/2013 – 06/2014, Military Fellow, Council on Foreign Relations, New York, NY.
- 07/2014 – Present, Chief, China, Mongolia, Taiwan Division, Joint Staff, J-5 Pentagon,
Washington, D.C.
FLIGHT INFORMATION
- Rating: Command Pilot
- Flight hours: More than 2,300
- Aircraft flown: B-2, B-52, T-38 and T-37
MAJOR AWARDS AND DECORATIONS
- Legion of Merit
- Defense Meritorious Service Medal
- Air Force Meritorious Service Medal with one oak leaf cluster
- Joint Service Commendation Medal
- Air Force Commendation Medal with one oak leaf cluster
- Air Force Achievement Medal with one oak leaf cluster
PUBLICATIONS
“A Micromovement Model with Bayes Estimation via Filtering: Application to Measuring Trading Noises and Trading Cost (co-author),” Nonlinear Analysis: Theory, Methods and Applications, 2006“Businessmen’s Risk Perception in China following the 1999 Chinese Embassy bombing and the 2001 EP-3 Incident,” doctoral dissertation, Proquest Dissertations, 2007.
EFFECTIVE DATES OF PROMOTION
- Second Lieutenant Oct 16, 1991
- First Lieutenant Oct 16, 1993
- Captain Oct 16, 1995
- Major Aug 1, 2002
- Lieutenant Colonel Mar 1, 2006
- Colonel Aug 1, 2011
- Current as of Dec 2015

Identifying Predictive Gray Zone Indicators Through People’s Values
Speaker: MacNulty, C. (DoD Consultant)
Date: July 2016
Christine MacNulty has forty years experience as a consultant in long-term strategic -planning for concepts as well as organizations, futures studies, foresight, and technology forecasting, technology assessment and related areas, as well as socio-cultural change. For the last twenty years, most of her consultancy has been conducted for the Department of Defense, including: The Joint Staff, OSD (OFT), the DON (Under Secretary, Secretariat, OPNAV N3/N5, N6, N7, CNET, NAVSEA, NAVSPECWARCOM, ONR, CNO’s SSG), the USMC (HQMC – Commandant), the USCG (HQ – Commandant), the USA (SMDC), JTAMDO, (then) BMDO, USSOCOM, (then) USACOM, JFCOM J9, and other COCOMs. She has also conducted projects for NATO ACT and NATO NEC, the British Army’s Force Development & Training Command, and the German BBK.
During the last thirty-five years Christine MacNulty has contributed methods and models for understanding social and cultural change. She developed the European version of SRI International’s Values & Lifestyles Program, and worked with the International Research Institute on Social Change to develop their social models. In the last twelve years she has applied her knowledge of strategy, cultures and cognition to “understanding adversaries” – using that information for planning and assessing non-traditional operations, information warfare, information operations, and strategic communication. She has also used these social models for training in network-centric operations and C2.
She was elected a Fellow of the Royal Society of Arts, Manufactures and Commerce in 1988 for her contribution to British industry. She is the coauthor of two books: Industrial Applications of Technology Forecasting, Wiley, 1971 and Strategy with Passion – A Leader’s Guide to Exploiting the Future, to be published in 07/2016. Her paper: “Method for minimizing the negative consequences of nth order effects in strategic communication actions and inactions” was published in NATO Defence Strategic Communications Journal, p 99, Winter 2015. Her monograph “Truth, Perception & Consequences” was published by the Army War College, 09/2007, and “Transformation: From the Outside In or the Inside Out” was also published by the Army War College in 09/2008. Her paper, Perceptions, Values & Motivations in Cyberspace appeared in the IO Journal, 10/03/2009, and The Value of Values for IO, SC & Intel was published in the 08/2010 edition of the IO Journal.

Question (S3): What must the coalition do in the information environment to achieve its objectives in Iraq and Syria and how can it deny adversaries the ability to achieve theirs?
Author | Editor: Spitaletta, J. (Johns Hopkins University Applied Physics Laboratory).
The following set of responses to Question S3 represent an attempt to distill the input from individuals who have contributed to any number of OSD-SMA efforts in recent years. Giordano’s Access, Assess, Engage (AAE) framework will be used to categories these recommendations. The recommendations are an attempt to distill the concepts proposed in a set of recent OSD-SMA publications . CENTCOM may improve cognitive engagement by producing a broader, more expansive joint intelligence preparation of the operational environment (JIPOE). An expanded JIPOE (Joint Intelligence Preparation of the Operational Environment) could potentially identify the behaviors of target audiences necessary to achieve US objectives, to develop possible psychological effects and leverage operations as a cognitive scheme of maneuver that could lead to synchronizing actions and messages to achieve coalition objectives. Below is a very high-level summary — details are in the report.
Access
Determining the accessibility of a target audience, the sixth step in the doctrinal target audience analysis process), identifies how a particular audience may be reached through various media.
Assess
Employing the Strange Model of Centre of Gravity (COG) analysis to identify critical capabilities, critical requirements (CR) and associated critical vulnerabilities (CV) of the threat. This type of functional decomposition could identify cognitive aspects of the threat that are exploitable through the information dimension. Our working hypothesis is that the COG lies in the cognitive domain.
Engage
CENTCOM should consider the combination of informational and physical powers in concert with members of the interagency to drive CENTCOM actions through an operational narrative. Leverage existing MISO programs Actions and messages are synchronized to generate the behaviors necessary to achieve coalition objectives.
Demystifying Gray Zone Conflict: A Typology of Conflict Dyads and Instruments of Power in Colombia, 2002-present.
Author | Editor: Koven, B. (University of Maryland, START).
This case study elucidates the dynamics of Gray Zone conflict with particular emphasis on the role of non- state actors. It does so through a detailed examination of the most recent phase (2002-present) of Colombia’s internal conflict (1964-present). More specifically, this research analyzes conflict dyads occurring between different types of conflict actors. It further examines which types of dyads leverage which instruments of power and to what extent activities are Gray versus Black or White across each type of dyad and instrument of power. Consequently, this research will help practitioners determine which instruments of power warrant careful consideration in Gray Zone conflicts depending on the types of actors engaged in conflict. This investigation will also aid Special Operations Forces in determining which types of belligerents may make effective partners and which instruments of power they should train and equip these partners to implement.
This research substantially bounds the scope of what needs to be considered by state forces operating in these environments. Specifically, the analysis shows that aggregating by actor-type is effective and that actors of the same type (e.g. leftist insurgents) behave very similarly. Moreover, it reduces the number of instruments of power that need to be considered for each type of conflict dyad. Even though five of the six types of conflict dyads entail multiple instruments of power, and the most complex dyad (government versus insurgents) involves six of the seven instruments, the average type of conflict dyad includes just 2.5 of the seven instruments.
Furthermore, this analysis demonstrates that Colombia’s conflict is Gray. While, Gray Zone dynamics also include White and Black activities, five (Government versus Insurgents, Government versus BACRIM Syndicates, Insurgents versus Insurgents, Insurgents versus Paramilitaries, and Insurgents versus BACRIM Syndicates) of the six types of dyads involve Gray activities. Gray Zone activities are especially prominent in four (Government versus Insurgents, Insurgents versus Insurgents, Insurgents versus Paramilitaries, and Insurgents versus BACRIM Syndicates) of these cases. The only dyad (Government versus Paramilitaries) that did not include Gray activities was extremely short-lived and involved the paramilitaries quickly acquiescing to government pressure to demobilize.
While the approach adopted by this research entails myriad advantages, readers should be cautioned that Gray Zone conflicts are extremely complex. Practitioners ought to consider how an intervention against one type of conflict actor might affect other types of belligerents. Only by doing so will they avoid negative externalities such as inadvertently strengthening other combatants. Moreover, commanders must recognize that the successful use of certain tactics by the state or their proxies within one instrument of power (e.g. military), can have profound effects on the efficacy of their opponent’s use of other instruments (e.g. informational). Finally, this case provides numerous examples of government forces collaborating with various, violent non-state actors. While Special Operations Forces are especially well positioned to do so, this requires extensive situational awareness at the micro-level. Alliances are fleeting and the willingness to cooperate with Special Operations Forces varies both over space and time.
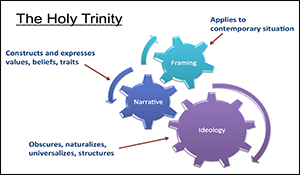
Strategic Communication and the Gray Zone: The Holy Trinity of Narrative, Ideology and Framing
Speaker: Ruston, S. (Arizona State)
Abstract
Date: June 2016.
Arizona State University’s Center for Strategic Communication conducts research on strategic communication challenges in the public sector, and has a long history of contribution to USG and DOD efforts in understanding narratives (especially extremist narratives), countering violent extremist ideology, and uniting humanities and social science analytic methods with computational capabilities to enhance speed and scale of analysis. This presentation discusses the “holy trinity” of strategic communication in gray zone conflicts—narrative, framing and ideology. Narrative creates scenarios that explain how events did unfold or should unfold. Framing guides interpretations to align facts with narratives. Narrative and framing accomplish ideological functions of naturalizing, obscuring, universalizing, and structuring. In addition to explaining these concepts we discuss the need for a model that predicts whether related messages are likely to gain traction with target audiences.
Dr. Scott Ruston (Ph.D., University of Southern California) is an Assistant Research Professor in the Center for Strategic Communication at Arizona State University where he specializes in narrative and media studies. He has applied this expertise in a variety of strategic communication research contexts, including new methods and tools for analysis of extremist narratives; strategies for counter or alternative narratives; and the neurobiology of narrative comprehension. He is co-author of “Mediated Martyrs of the Arab Spring” exploring narrative in new media contexts, and Narrative Landmines: Rumors, Islamist Extremism and the Struggle for Strategic Influence which examines rumors as narrative phenomena. In addition, Dr. Ruston is a 24-year veteran of active and reserve service in the US Navy, having deployed to Combined Joint Task Force Horn of Africa as the J39 and Deputy Director for Theater Security Cooperation, as well as past support through NATO ACT of the Multi-National Information Operations Experiment (MNIOE). Dr. Ruston brings this experience to the study of real world problems of strategic communication in public diplomacy and defense contexts.

The Strategic Uses of Ambiguity in Cyberspace
Speaker: Libicki, M. (Naval Academy)
Date: July 2016
Martin Libicki (Ph.D., U.C. Berkeley 1978) holds the Richard Keyser Distinguished Professor of Cyber Studies at the U.S. Naval Academy. He wrote three commercially published books, Cyberspace in War and Peace (USNI Press, forthcoming autumn 2016), Conquest in Cyberspace: National Security and Information Warfare (2007), and Information Technology Standards: Quest for the Common Byte (1994). As senior management scientist at RAND (1998-2016) he wrote numerous monographs, notably Defender’s Dilemma, Brandishing Cyberattack Capabilities, Crisis and Escalation in Cyberspace, Global Demographic Change and its Implications for Military Power, Cyberdeterrence and Cyberwar, How Insurgencies End (with Ben Connable), and How Terrorist Groups End (with Seth Jones). Earlier employment includes adjunct professorships at Columbia University and Georgetown University, 12 years at the National Defense University, three years on the Navy Staff as program sponsor for industrial preparedness, and three years for the GAO.
To what extent do populations maintain positive views of ISIL or ISIL’s ideology, particularly in European, N. African, and Arabian Peninsula countries most associated with foreign fighter flows into Syria and Iraq? What are the general perceptions associated with ISIL endorsed themes, to include: 1) desire for re-establishing the Caliphate; 2) imposition of Shariah law; 3) belief that the Ummah/Islam is under attack from the West; 4) low tolerance for non-Sunni Muslim ethno-religious groups; and 5) negative disposition towards gender equality?
Author | Editor: Canna, S. (NSI, Inc).
Executive Summary
There is ample evidence that by and large Muslim populations in the MENA region and Europe do not view ISIL favorably (see QL 3). However, there are many similarities and a few significant differences among these populations regarding the credibility and salience of many of the messaging themes that ISIL espouses.
Arabian Peninsula
In Syria and Iraq, one of the largest groups of foreign fighters come from Saudi Arabia, raising questions about the overall level of support for ISIL among the general population. Generally, Sunnis in the Arabian Peninsula support Salafist and Islamist political agendas but reject ISIL’s claims to political and religious legitimacy (Lynch; Aguero). According to Tom Lynch, Distinguished Research Fellow at National Defense University, political Islam, which seeks to introduce conservative Islamic practices into the political sphere, is far more popular than the implementation of ultra-conservative Salafism as espoused by ISIL.
Most Sunni Muslims in the Arabian Peninsula do not believe a caliphate is necessary to implement conservative Muslim political and social thought (Aguero). However, they share some of the same grievances about government that gave rise to ISIL in Iraq and Syria. An Anonymous academic, argues that the Arab Spring showed that populations in the Arab world are rejecting what they see as a dysfunctional system of governance across the region. There is a demand for greater participatory governance, social justice, and better economic opportunities. At the same time, however, they are supportive of the implementation of Sharia law, including low tolerance for gender equality and non- believers (Anonymous; Aguero). But it is important to keep in mind, particular in Muslim- majority countries, that Sharia is considered to be a way of life, not merely a legal code (Aguero). According to a 2014 Pew poll,1 making Sharia the law of the land has 74 percent support in the MENA region.
Populations in the Arabian Peninsula strongly oppose westernization and modernization, seeing it as an attack on Sunni Muslim unity and heritage. Lynch argues that these populations can be animated towards short-term support for violent causes when they perceive non-Sunnis or non-Muslims to be attacking fellow Sunni Muslims. This helps explain why groups like ISIL can gain meaningful, short-term support in moments of perceived danger for Sunni Muslims. For example, 83% of Saudis consider Western cultural invasion to be a very important or important problem (Moaddel, 2013; Aguero). Furthermore, 84% of Saudis also ascribe to the belief that the Ummah and/or Islam is under attack by the West.
In the past, Salafists from the Arabian Peninsula have provided material and financial support to Salafist jihadi groups opposing Bashar al Assad in Syria, according to Lynch. This anti-Assad support has also aided the rise of ISIL both directly and indirectly. Most Salafist support for ISIL has withered but some support still finds its way to ISIL.
Mia Bloom, an expert on the nexus between women and terror, noted that ISIL is careful to shape its messaging in ways that resonate best with various female population groups. English messaging focuses on giving women in the West a frontline role in the combat, such as the Al-KhansaaBrigade. Meanwhile, Arabic messaging offers women more socially acceptable roles as wives and mothers. This is particularly the case in messaging to women in Tunisia where women are seeking romance and adventure (at a time when marriages are delayed due to poor economic conditions). In Saudi Arabia, the messaging is more about empowering women by showing women in ISIL-controlled territories (in full niqab) driving cars.
Dr. Lynch concludes that the bottom line is that the depth and durability of conservative Islam in the Arabian Peninsula means that even if ISIL is degraded or defeated, the preconditions for another Salafi jihadist group to rise in its place will remain present for the foreseeable future.
Europe
Muslim populations in Europe overwhelmingly reject ISL’s ideology and violent tactics (see Quick Look 3). However, a small percentage of Muslims—particularly youths—actively or passively support ISIL’s ideology and political objectives according to Marc Pierini, a visiting scholar at Carnegie Europe and former career EU diplomat.
What we know about support for ISIL in Europe is that most supporters are relatively young (between 18-30 years of age), have experienced an identity crisis, are disconnected from their communities, and are marginalized within their own European societies, which have failed to integrate their cultural preferences into the European social fabric. In Britain, sympathizers tend to be highly educated while sympathizers in France and Belgium are often school dropouts, delinquents, have family problems, and face social exclusion and isolation, according to Pierini. What is also common among supporters of ISIL in Europe is that many of them have a superficial understanding of Islam, and are perceived by ISIL recruiters to be easy to co-opt and indoctrinate according to Pierini.
Many Muslim families in Europe still hold traditional values even decades after living in Western Europe—according to Pierini and Mark Caudill of the USMC Center for Advanced Operational Culture Learning—including negative disposition towards gender equality and belief that Muslims are under attack from the West. What is clear, though, is that there is a generational divide where youth have a greater sense of frustration with their place in society compared to their parents. This is due, in part, to record high youth unemployment in Europe.
Among disaffected youth in Europe, the Caliphate has appeal, according to Pierini and Raffaello Pantucci of RUSI. The Caliphate provides disaffected youth with a purpose, a sense of belonging, and an outlet for their frustrations, outlined Pierini. Recruitment of young Europeans by jihadist movements abroad is not new (e.g., Afghanistan), but the scale is unprecedented due in large part to ISIL’s massive and modern propaganda campaign layered upon economic and social frustrations of Europe’s Muslim youth.
The appeal has waned in some degree as ISIL loses territory, Pantucci wrote. Its visible loss has led to a gradual loss of appeal and is one of the reasons for the reduction of foreign fighters from Europe.
What is dangerous is that ISIL is intentionally seeking to exacerbate tensions between mainstream and Muslim communities in Europe, according to Pierini. They do this through recruitment of European youths as foreign fighters, facilitate attacks that exacerbate anti- Muslim sentiment, and actively nurture sectarian divides between these two communities. This inculcates a growing sense of uncertainty and powerlessness in the face of repeated ISIL-supported attacks and is shifting a segment of society towards extreme right/xenophobic political parties and movements. The migration/refugee crisis out of Syria exacerbates these tensions, Pierini argues.
Africa
Like most of the Muslim world, support for ISIL in Northern Africa is quite low (Feuer). In 2014, an International Republican Institute poll found that only one percent of respondents believe that Tunisians should be joining Daesh. However, aspects of ISIL’s ideology finds broader support in Tunisia, especially when expressed in generic terms, including the incorporation of Sharia law, a nostalgic approval of the idea of a Caliphate—even though there is little support for the erosion of the nation state, and a belief that Islam is under attack from the West.
Similarly, there is very little support for ISIL in the Sahel, but other Islamist extremist groups do operate in the area, according to Paul Melly, a Sahel expert at Chatham House. In general, popular support for extremists groups in the region is strongly driven by local conditions and politics rather than ideology. Another characteristic of extremist groups in the Sahel is their more extensive ties and crossover between extremist groups and criminal organizations. The largest transnational group in Mali is al Qaeda in the Islamic Maghreb (AQIM), but it is largely considered a foreign organization that does not match well with the local population’s Sufism. Other groups operating in the area, who draw support based on ethnic or familial ties, is Haut conseil pour l’unité de l’Azawad (HCUA) and Mouvement pour l’unicité et le jihad en Afrique de l’Ouest (MUJAO). Aside from familial or ethnic ties, other reasons that individuals join these groups include poor economic opportunities, anti-state ideas, and the breakdown of traditional society.
Contributors
Hassan Abbas (NDU), Shane Aguero, (US Army), Mia Bloom (GSU), Mark Caudill (USMC Center for Advanced Operational Culture Learning), Alexis Everington (MSI), Sarah Feuer (Washington Institute for Near East Policy), Tom Lynch (NDU), Paul Melly (Chatham House), Raffaello Pantucci (RUSI), Marc Pierini (Carnegie Europe)

