SMA Publications
NSI maintains an extensive Publications archive of government-sponsored research and analysis products, various research efforts from our professional and technical staff, and a variety of corporate news items. The government-sponsored products are maintained on behalf of the US Department of Defense (DOD) Strategic Multilayer Assessment (SMA) program and address challenging national security problems and operational imperatives.
Understanding Megacities with the Reconnaissance, Surveillance, and Intelligence Paradigm.
Author | Editor: Ehlschlaeger, C. (ERDC).
Given the challenges of declining DOD budgets while improving our ability to monitor megacity populations, this white describe many of the issues facing the DOD for phase zero operations and collecting theinformation necessary should conflicts escalate.
The overriding goal of this White Volume is how to best understand the changing population, infrastructure, and environment in complex urban environments so that we can respond to both short‐ and long‐term national security challenges. The SMA research project “Megacity Reconnaissance, Surveillance, and Intelligence Project: Dhaka Pilot” uses the term `Megacity’ in its title to reflect the challenges of under‐ standing rapidly changing urban environments. SMA chose Dhaka, Bangladesh for the case study because Dhaka is one the quintessential urban spaces that traditional DoD socio‐cultural techniques would find most challenging to understand. Dhaka is one of the fastest growing cities in the world, a megacity with no indication that its growth rate will decline.
This White Volume explores issues relevant to understanding urban populations, both today and years from now, and the stability indicators that will help to monitor insecurity and prevent potential crises around the world. While the U.S. Government has long monitored the stability of other regimes, it does not have a long history of extensively monitoring other populations except when U.S. troops are deployed overseas. For example, the South Vietnamese military and the U.S. Army works side‐ by‐side extensively measuring and monitoring populations in rural areas prone to Vietcong activities. This very labor intensive survey was stored in a database man‐ agement system and quantitatively analyzed. It was statistically shown that the col‐ lection and use of this database reduced violence in areas with data collected com‐ pared to similar areas not monitored. Monitoring populations using human terrain teams or U.S. and Partner Nation military units, however, is both risky and labor in‐ tensive. Thus, existing population monitoring in Afghanistan and Iraq cannot be per‐ formed across the entire globe due to their costs. It is necessary to change the way we collect, integrate, and disseminate population information to achieve short‐ and long‐term national security goals.
The White Volume’s authors represent practitioners and researchers with extensive experience in their respective fields. While we were unable to include all the experts desired for this effort, the White Volume contains a broad spectrum of perspectives for better understand urban environments. The chapters are organized from the more theoretical and philosophical to the more technical. The following brief de‐ scription of these papers provides an overview of each chapter, but doesn’t express all the content contained within.
Dr. James Knotwell’s “Megacity Place‐Centric Population Analysis” begins the White Volume with a discussion on the need for cultural understanding in RSI using the “Fundamental Four” cultural descriptors. He points out the Fundamental Four doesn’t account for the “analysis of place”, or how geography affects culture. Dr. Knotwell discusses in detail how socio‐cultural analysis could be improved by better understanding of geographic analysis of place.
Next, Marc Imhoff et al.’s “Evaluating Long‐Term Threats to Environmental Security via Integrated Assessment Modeling of Changes in Climate, Population, Land Use, Energy, and Policy” chapter discusses regional environmental security forecasting energy, water scarcity, and climate changes far into the future.
In the third chapter “Understanding Megacities‐RSI – Dhaka’s Design as an Expres‐ sion of Culture & Politics,” Dr. David Ellis and James Sisco explore the socio‐cultural dynamics of Dhaka, Bangladesh from the community level, mahallas, upwards to better understand instability indicators. The chapter discusses the tension between political, religious, and social aspects of the unplanned megacity.
Douglas Batson’s chapter on land tenure and property rights in megacities discusses rural‐to‐urban migration and the piratical power grabs associated with slum for‐ mations. It examines ungoverned urban spaces and the process of building human security by improving poor peoples’ hold on land. Finally, the chapter discusses three tools that will aid in identifying and understanding who occupies and controls megacity spaces.
In the fifth chapter, “Urban Socio‐Cultural Monitoring with Passive Sensing,” Michael Farry et al. propose that passive sensors located in difficult to assess urban envi‐ ronments will provide actionable intelligence in local or tactical situations. The au‐ thors analyze how various measurable social signals can be applied to PMESII vari‐ ables. The use of small sensors, while potentially problematic if used in phase zero environments, could provide valuable information in ungoverned urban spaces when supported by partner nation governments.
While other chapters in this White Volume discuss ways to represent populations geographically or culturally, Randy Pearson’s “A Network‐based Approach to Na‐ tional Security” raises the challenges of understanding illicit financial networks. Pearson discusses the trans‐dimensionality of illicit networks, and the difficulty of representing this information for DOD operational planning. The complexity of fi‐ nancial networks is not an uncommon one for socio‐cultural analysis. Socio‐cultural systems cannot be easily represented in any of the traditional quantitative visualiza‐ tion methodologies (I.e., thematic maps, topographic maps, networks) because the number of dimensions of socio‐cultural factors is greater than what can easily be readily seen.
In Chapter Seven, “Evaluating Slum Severity from Remote Sensing Imagery,” Dr. Karen Owen discusses original research demonstrating remote sensing techniques that will help identify neighborhood‐scale socio‐cultural information in urban areas, especially economic variability. While the techniques require calibration for each megacity, the research provides excellent direction for experienced remote sensing professionals.
Chapter Eight, “Modeling the Discourse of Megacities: Assessing Remote Populations in the Non‐Western Worlds,” Dr. Kalev H. Leetaru & Dr. Charles Ehlschlaeger discuss the ramifications of collecting information from the internet in order to understand megacities. They argue that while megacities have unique geographic and social characteristics, the tools and techniques for understanding communication remain the same but that additional foundational information will ease the difficulty of monitoring urban areas in the RSI paradigm.
Chapter Nine, “How Semi‐Automated Analysis of Satellite Imagery Can Provide Quick Turn‐Around Economic and Environmentally Relevant Answers to Large Scale Questions”, by Ms. Ida Eslami et al., provides a technical discussion on re‐ search that can greatly benefit the RSI paradigm. The goal of their research is to de‐ velop techniques for taking satellite imagery and processing it to actionable infor‐ mation. Their technique mainly uses MODIS satellite products updated every 16 days in order to monitor changes and trends over time. Possible socio‐cultural ap‐ plications include urbanization, crop abundance & predicted yields, and the availa‐ bility of natural resources. Given the challenges of monitoring megacities around the world in phase zero, automated techniques will be necessary to derive information from the copious amounts of data collected from satellites and the internet.
The final chapter, “UrbanSim: Using Social Simulation to Train for Stability Opera‐ tions,” Ryan McAlinden et al. discuss modeling urban environments for training. Social and cultural modeling plays a critical role in advancing our situational under‐ standing of these complex, interwoven environs. Academia, government and indus‐ try all continue to make advancements in developing accurate models of human be‐ havior, though significant challenges still remain. These challenges are presented in the context of an existing training application for teaching Battalion commanders how to successfully navigate complex, multifaceted missions where the populace is the cornerstone to success.
Contributing Authors
LTG Michael T. Flynn (DIA), Mr. Douglas E. Batson (NGA), Dr. Eliza Bradley (NGA), Ms. Jill Brandenberger (PNNL), Mr. Bruce Bullock (CRA), Dr. Katherine Calvin (PNNL), Dr. Leon Clarke (PNNL), Dr. James Edmonds (PNNL), Dr. Charles R. Ehlschlaeger (ERDC), Dr. David Ellis (GBH), Ms. Ida Eslami (NGA), Mr. Michael Farry (CRA), Mr. Sean Griffin (NGA), Dr. Mohamad Hejazi (PNNL), Dr. Kathy Hibbard (PNNL), Dr. Randall Hill (USC), Dr. Marc Imhoff (PNNL), Dr. James Knotwell (KG), Mr. Kalev H. Leetaru (GU), Mr. Ryan McAlinden (USC), Dr. Karen Owen (NGA), Mr. Randy Paul Pearson (USNORTHCOM), Dr. Jonathan Pfautz (CRA), Dr. David Pynadath (USC), Mr. James Sisco (GBH), Ms. Allison Thomson (PNNL)

The ‘New’ Face of Transnational Crime Organizations (TCOs): A Geopolitical Perspective and Implications for US National Security.
Author | Editor: Riley, B. (OSD/RRTO), Kiernan, K., St. Clair, C. (Kiernan Group) & Canna, S. (NSI, Inc).
Office of the Secretary of Defense
President Barack Obama: Significant transnational criminal organizations constitute an unusual and extraordinary threat to the national security, foreign policy, and economy of the United States, and I hereby declare a national emergency to deal with that threat…Criminal networks are not only expanding their operations, but they are also diversifying their activities, resulting in a convergence of transnational threats that has evolved to become more complex, volatile, and destabilizing.
Department of Defense Counternarcotics and Global Threats Strategy, 27 Apr 11: The 2011 White House Strategy to Combat Transnational Organized Crime defines TCOs as “self- perpetuating associations who operate transnationally for the purpose of obtaining power, influence, monetary and/or commercial gains, wholly or in part by illegal means, while protecting their activities through a pattern of corruption and/ or violence, or while protecting their illegal activities through a transnational organizational structure and the exploitation of transnational commerce or communication mechanisms.”
Transnational organized crime and transnational criminal organizations refer to a network or networks structured to conduct illicit activities across international boundaries in order to obtain financial or material benefit. Transnational organized crime harms citizen safety, subverts government institutions, and can destabilize nations.
James R. Clapper, Director of National Intelligence: Transnational organized crime is an abiding threat to U.S. economic and national security interests, and we are concerned about how it might evolve in the future. We are aware of the potential for criminal service providers to play an important role in proliferating nuclear- applicable materials and facilitating terrorism.
National Intelligence Council: Five key threats to U.S. National Security: (1) Transnational Organized Crime (TOC) Penetration of State Institutions; (2) TOC Threat to the U.S. and World Economy; (3) Growing Cybercrime Threat; (4) Threatening Crime-Terror Nexus; and (5) Expansion of Drug Trafficking (Mexican drug trafficking organizations continue to expand their reach into the United States.)
Department of Defense Counternarcotics and Global Threats Strategy: Transnational organized crime represents a significant, multilayered, and asymmetric threat to our national security…It is not viable for DOD to continue to examine this complex threat through the single lens of the drug trade.
General Martin Dempsey, Chairman of the Joint Chiefs of Staff, in an interview with NBC’s Ted Koppel on January 24th, 2013: …what we’ve had to do in response is we have become a network. To defeat a network, we’ve had to become a network…
General Stanley McChrystal, March/April 2011 edition of Foreign Policy: …to defeat a networked enemy we had to become a network ourselves. We had to figure out a way to retain our traditional capabilities of professionalism, technology, and, when needed, overwhelming force, while achieving levels of knowledge, speed, precision, and unity of effort that only a network could provide…
The continually evolving strategic environment coupled with the ascendant role of Transnational Criminal Organizations (TCOs) necessitates a comprehensive understanding of these organizations. TCOs represent a globally networked national security threat and pose a real and present risk to the safety and security of Americans and our partners across the globe. This challenge blurs the line among U.S. institutions and far surpasses the ability of any one agency or nation to confront it. Thus, countering TCOs necessitates a whole-of-government approach and, beyond that, vibrant relationships with partner nations based on trust. These are essential if the U.S. is to remain the partner of choice and effectively counter TCOs globally. Weak and unstable government institutions coupled with scarce legitimate economic opportunities, extreme socio-economic inequities, and permissive corrupt environments are key enablers that allow TCOs to operate with impunity. These same factors enable the emergence of violent extremist organizations (VEOs). The potential nexus between VEOs and TCOs remains an area of deep concern. In this context, deeper insight into the contemporary face of TCOs will facilitate the development of strategies to counter and defeat them. This white volume examines the “new” face of these transnational crime organizations and provides a geopolitical perspective and implications for U.S. national security. The nexus of culture and technology (including modern communication technologies) and their impact on the evolution of TCOs is discussed in addition to their implications for countering TCOs.
Key Insights
- Nature of Transnational Criminal Organization (TCO) threat
- TCOs represent a globally networked national security threat and pose a real and present risk to the safety and security of Americans and our partners across the globe.
- The struggle against TCOs is a long-term proposition, requiring continuous effort, creative solutions, and the assumption of some risk.
- This challenge blurs the line among U.S. institutions and far surpasses the ability of any one agency or nation to confront it.
- The specific threats vary by region and sub-region.
- Many regions are plagued by a drug arm that is vibrant, expanding, and has both a solid supply and demand base.
- In many instances, criminal groups seem to be evolving towards a business model based on loose associations of individuals or small groups operating independently.
- Successful TCOs appear to adapt their operations to local conditions and geography.
- They utilize local resources and capabilities, outsource and enter alliances to further their interests, and rely on both local and global ethnic communities to network and operate.
- The connection of a TCO with a legal business operation lends an element of legitimacy to the group’s other activities.
- They operate legitimate businesses as front companies to help launder money associated with illegitimate activities.
- Members and senior leaders may participate in public or private political, charitable, or social events attended by highly placed political, business, and community leaders.
- They exploit legitimate commerce and, in some cases, create parallel markets.
- TCOs represent a globally networked national security threat and pose a real and present risk to the safety and security of Americans and our partners across the globe.
- Key enablers that allow TCOs to operate with impunity include
- weak and unstable government institutions that have limited reach and presence into the furthest corners of society;
- scarce legitimate economic opportunities that entice citizens to cooperate with TCOs for security and economic well-being;
- extreme socio-economic inequities that open some geopolitical regions to a much greater risk of criminal or ideological manipulation and growth than others;
- permissive environments, loose financial controls, widespread corruption, and fraudulent document facilitation networks;
- extreme interconnectedness and gaps in socio-economic and political equity creating and overall environment favorable to the formation and continued growth of TCOs; and
- globalization via Information and Communications Technologies (ICT) transforming an increasingly hyper-connected markets and economies blur boundaries and even authority across socio-political processes and State control.
- Recent analytical work based on empirical data indicates, however, that a large percentage of the countries where convergence between TCOs and VEOs is prominent are among the richest in the world. The reason for this might be that TCOs and VEOs converge in their mutual interest to create and operate in ungoverned spaces despite having different ends.
- Bottom line: The ability of TCOs to use violence or threat of violence to achieve their aims renders no one immune irrespective of governance because all system are vulnerable from a micro or individual level
- Nexus of TCOs and Terrorist Organizations
- In many war zones and in ungoverned spaces across the globe, criminal and terrorist groups have formed once-improbable relationships, finding new ways to collaborate with each other.
- Environments most conducive to the formation and support of TCOs possess the same characteristics as those favorable to VEOs.
- Organized crime not only sustains insurgencies from a financial standpoint, it also supports their asymmetric warfare campaigns.
- This VEO/TCO convergence can be tremendously corrosive and also self- reinforcing.
- On the other side of the coin, an insurgency can lose both its standing with the population and its internal sense of political identity because of criminalization. This can be exploited in a counterinsurgency campaign.
- However, not in all instances is there such a proven nexus and in many instances, the degree of overlap is difficult to determine.
- Recent analytical work based on empirical data indicates that interconnectivity is greater than one might have predicted.
- Hybrid organizations (those that include both political extremist and criminal elements) are more of a threat across threat domains (radiological/nuclear [RN] smuggling, RN smuggling with extremist organization involvement, nexus formation, and instability threat) than are the more purely criminal organizations.
- In many war zones and in ungoverned spaces across the globe, criminal and terrorist groups have formed once-improbable relationships, finding new ways to collaborate with each other.
- Top level considerations to countering and defeating TCOs
- Countering TCOs is defined as the means to detect, counter, contain, disrupt, deter, or dismantle the transnational criminal activities of state and non-state adversaries threatening U.S. and partner nation national security. This will require the following:
- dismantling their networks across the globe and driving down their impacts to levels that can be handled by local law enforcement organizations;
- fostering a transnational, cross-organizational response and development of strategic security partnerships;
- coordinating intelligence and law enforcement actions between organizations and sharing data from a variety of organizations across the globe to identify criminal networks and activities;
- developing a comprehensive Counter Threat Network approach, whole-of- government, whole-of-societies collaboration, and possibly even new structures; and
- deploying teams of globally focused financial and fraud investigators to follow the illicit money supporting TCO and insurgent networks.
- Recent analytical work based on empirical data suggests that it is difficult to disrupt the activities of the global network by targeting a few kingpins and that the most effective means of countering such a global illicit network should involve a mixture of tools used to counter criminal activity in conjunction with those used to counter terrorism.
- Whole-of-governmentapproach
- Combating Transnational Criminal Organizations (CTCO) activities are primarily interagency in nature with many authorities, capabilities, and capacities beyond the scope of DOD requiring a whole-of-government approach.
- Taking the whole-of-government approach in support of law enforcement agencies has helped build a cooperative partnership of networks to counter transnational organized crime.
- The USG needs to develop a doctrine for stabilizing territories plagued by the crime-terror nexus and putting a focus on de-conflicting the work of disparate U.S. agencies, and crafting holistic strategy.
- The USG needs to create trans-agency teams that would integrate military forces, diplomats, reconstruction and development specialists, and legal experts tasked with reestablishing the authority, legitimacy, and effectiveness of the state in a target zone.
- However, barriers remain to achieving a universal realization of TCOs as a true threat to homeland security.
- Sometimes interagency legal wrangling, sensitivities, parochialism, diminishing resources, and old-fashioned bureaucracy stymie U.S. responses.
- Specific DOD role
- DOD brings to the government unique capabilities including
- comprehensive, disciplined, and finely developed capacity to develop complex strategic plans;
- global reach as well as unique and substantial resources;
- collaborative partner capacity building;
- certain counternarcotics authorities to assist law enforcement agencies;
- capability to detect and monitor illicit trafficking and disrupt the illegal flow of precursor chemicals; and
- intelligence analysis and information sharing.
- There is, however, a lack specific knowledge of those capabilities and the processes used to obtain them within the interagency.
- Improvements in key areas are identified:
- training programs to educate DOD analysts and planners on how organized criminal groups operate and how law enforcement and other governmental groups counter organized crime;
- assigning more representatives from U.S. government agencies and organizations involved in combating organized crime to DOD organizations; and
- reviewing and streamlining authorities pertaining to DOD’s support to law enforcement as well as regulations regarding the sharing of intelligence information.
- DOD brings to the government unique capabilities including
- Role of partner nations
- Building the capacity of our partners to exercise their territorial sovereignty is crucial.
- Vibrant relationships based on trust are essential if the U.S. is to remain the partner of choice and effectively counter TCOs globally.
- Role of strategic communication in CTCO
- Strategic communication should rise to the level of main focus in many instances rather than remain a supporting effort with unachieved potential.
- Countering TCOs is defined as the means to detect, counter, contain, disrupt, deter, or dismantle the transnational criminal activities of state and non-state adversaries threatening U.S. and partner nation national security. This will require the following:
- The nexus of culture and technology in the evolution of TCOs and implications for countering CTO strategies: an evolutionary biological perspective
- The socio-technical nature of globalization is no longer treatable as separate elements.
- Current and future TCOs will be geographically and culturally dispersed.
- They will exhibit different socio-political tendencies and values.
- They will evolve different socio-technical infrastructures to support and protect their activities.
- They will mutate in response to environmental pressures ranging from market opportunities to government stability and even emergence of other criminal or VEO groups.
- Multiple and repeated interactions between system entities and individuals generate macro-level characteristics and dynamic patterns not found at the micro-level.
- They will operate as fully developed platforms for innovation that compete violently with each other and provide deviant entrepreneurs key advantages.
- The result is a strategic environment where disruptive ideas rapidly become products or processes that are tested in the real world very fast; success is easily imitated and iteratively improved.
- Modern communication technologies together with the explosion of electronically available information have
- hyper-connected markets and societies across the globe;
- enabled expansion of TCOs into emerging markets; and
- allowed TCOs to rapidly recruit expertise and employ various skills on a temporary or transient basis without the need to formally augment their enterprise. (Similarly, VEOs may recruit and sway sympathetic individuals without relying on old methods of radicalization or complete indoctrination to the cause.)
- Technological breakthroughs and their impact
- Advances in additive manufacturing, online anonymity, anonymizable currencies, and communication technologies amongst others have the potential to change the contours of the landscape entirely.
- They increase the potential for violent upheaval and instability because they empower greater numbers of individuals
- Modern communication technologies make it much more difficult for law enforcement to monitor and/or trace communications and financial flows among nodes in the networks.
- Implications for countering TCOs
- Deviant innovators have one essential business requirement: to be one step ahead of the governmental deployment of interdiction technologies to remain a profitable operation while being ready to hack new inventions as soon as they are deployed.
- This necessitates that governments respond accordingly
- The USG should constantly play the role of TCOs, penetrating governmental technologies.
- Policies should be designed in a way that whenever the environment changes, the shape of the governmental response can change with it.
- Think at the scale of big technology trends, devaluing the importance of any individual adaptation in any threat assessment.
- Cyberspace offers a solution in terms of collaboration environment providing CTCO groups a data ecosystem that is fluid enough to let organizations innovate from the bottom up in response to local conditions. On the other hand, balancing competing needs for security and access provide scaffolding for an entire range of cyber-enhanced capabilities. This three-element structure allows coordination and collaboration in local spaces, as well as global data sharing.
- A better fundamental characterization of the cyber-socio-technical nexus can help form cogent U.S. defense-related policies and guidance for operational context.
- The socio-technical nature of globalization is no longer treatable as separate elements.
Contributing Authors
Mr. Gary Ackerman (START); Maj David Blair (USAF/Georgetown University); Ms. Lauren Burns (IDA); Col Glen Butler (USNORTHCOM); Dr. Hriar Cabayan (OSD); Dr. Regan Damron (USEUCOM); Mr. Joseph D. Keefe (IDA); Col Tracy King (USMC); Mr. David Hallstrom (JIATF West); Dr. Scott Helfstein (CTC); Mr. Dave Hulsey (USSOCOM); Mr. Chris Isham (JIATF West); Ms. Mila Johns (START); Mr. James H. Kurtz (IDA); Dr. Daniel J. Mabrey (University of New Haven); Dr. Vesna Markovic (University of New Haven); MG Michael Nagata (Army, J-37); Dr. Rodrigo Nieto-Gomez (NPS); Ms. Renee Novakoff (USSOUTHCOM); Ms. McKenzie O’Brien (START); Dr. Amy Pate (START); Ms. Gretchen Peters (George Mason University/Booz Allen Hamilton); Mr. Christopher S. Ploszaj (IDA); BG Mark Scraba (USEUCOM); Mr. William B. Simpkins (IDA); Dr. Valerie B. Sitterle (GTRI); Mr. Todd Trumpold, (USEUCOM); Mr. Richard H. Ward (University of New Haven); Mr. Tom Wood (JIATF West); Dr. Mary Zalesny, (CSA SSG, PNNL)

7th Annual SMA Conference: Over a Decade into the 21st Century…What Now? What Next?
Author | Editor: Canna, S. & Popp, G. (NSI, Inc).
The 7th Annual Strategic Multilayer Assessment (SMA) Conference was held at Joint Base Andrews from 13-14 November 2013. The conference was focused on global megatrends and their implications in all spheres of national security. It is no exaggeration to state that the world today is a very different place than it was barely 12 years ago when the war against al Qaida and its affiliates began. As we move forward, continuing advances in various spheres such as the sociotechnical world will present both challenges and opportunities. The conference examined these and related themes and highlighted new insights from the social and neurosciences.
As in previous years, the conference addressed the needs of the Geographical Commands. Representatives from the Commands discussed their pressing needs and key operational requirements so that SMA’s wide network of experts could assist in identifying capabilities that match these needs.
Findings from Panel Discussions
Guest speaker Brig. Gen. David B. Béen, Deputy Director, Special Actions and Operations, J-3, spoke about the unique ability of SMA to bring together representatives from a diverse community—including from the DOD, academia, industry, media, etc.—to address core requirements of the Combatant Commands (COCOMS). This community can help the DOD succeed in its main duties: 1) being mindful of future threats to the United States and 2) exploiting emerging opportunities to make the world a more stable place. The DOD has a responsibility to engage in rigorous analysis, informed debate, and top-flight research with partners. Members of the SMA support community also bear certain responsibility to build relationships, learn more about operational needs, and apply their considerable talent to help operators achieve mission success.
Guest speaker Mr. Earl Wyatt, Rapid Fielding Office, Office of the Assistant Secretary of Defense for Research and Engineering, spoke about the need to bring various resources from across the government, industry, and academia to bear on DOD’s objectives. The force of the future will be leaner, more agile, more flexible, and technologically advanced. While U.S. forces will be called on to do more with less, this is not a down time for innovation; it is a challenge to do more with less. The DOD will be particularly challenged to engage in innovative thinking to mitigate threats in nonkinetic ways. Partner capacity will be key to this conversation. The DOD is moving toward a more balanced prototyping portfolio to include developmental as well as operational prototyping to provide a hedge against technical uncertainty or unanticipated threats; enhance interoperability and reduce lifecycle costs; and explore the realm of the possible without commitment of follow-on procurement.
Guest speaker Mr. Ben Riley, Rapid Fielding Office, Office of the Assistant Secretary of Defense for Research and Engineering, spoke about the value SMA provides to the DOD by bringing together a diverse group of academic and technical perspectives on difficult problems. However, the DOD still needs to open its aperture more widely to encounter new ideas and perspectives. In a time of resource constraint, there is a tendency to circle the wagons around traditional defense programs, but it is important to continue to engage in rigorous, innovative, and unexpected thinking to meet the commanders’ needs.
Keynote speaker, LTG Michael Flynn, Director, DIA, spoke about accelerating change in the defense intelligence community. The two big challenges facing the defense intelligence community are skyrocketing demand and resource reduction. In order to meet the two challenges, the DIA needs to restructure and adapt. The DIA needs a new model to prepare the foundation that provides U.S. forces with agility, flexibility, and resiliency. The USG must be prepared for unknown, highly complex, uncertain environments. One failure of the last decade has been our limited ability to understand the operational environment, which led to mismatch in resources and capabilities. This failure needs correction in order to meet the challenges of tomorrow.
Panel One discussed the use of religious engagement by the United States to improve global prospects for peace. It is important that the USG engages the full realm of social actors when trying to understand operational environments. Within this group, religious leaders are some of the most influential actors—specifically in Muslim communities. In many cases, religious leaders are more credible than the highest-ranking political officials in that community are. U.S. organizations like the Special Envoy to the OIC have committed to religious engagement in areas including healthcare, maternal health campaigns, religious freedoms, and countering violent extremism. The panel agreed that the commitment by the United States to continued religious engagement in these areas and beyond is crucial. Furthermore, the United States must ensure that its religious engagement efforts are viewed as legitimate by the local communities in the places where the religious engagement is taking place.
Panel Two discussed four significant megatrends likely to emerge in the next decade: demographic change, resource stress, further diffusion of power, and individual empowerment. There are two particularly relevant projections that support the diffusion of power megatrend: 1) by 2030, Asia will have surpassed the United States and Europe in power and size while Europe, Japan, and Russia continue to decline, and 2) by 2030, the international system will transition from hegemony to multi-polarity. With regard to the resource stress megatrend, competition and scarcity involving natural resources are emerging as security threats for the United States and its allies. U.S. allies are particularly vulnerable to natural resource shock. The perfect storm involves youth bulge, unemployment, ability to organization through information technology, and a food shock. Furthermore, the convergence of multiple trends means individuals and groups are angrier and more dangerous. With regard to demographics, the most relevant finding for the USG is that the ratio between young adults and older adults in some of the world’s most unstable regions is declining, which statistically suggests greater stability and democracy in the coming decades. However, some of the countries that the USG is, or has been, most involved in still have high fertility rates and very youthful populations.
Panel Three examined the current era and why it is special. First, it has produced an increasing number of mega-issues. Mega-issues are not simply larger public policy issues; they are significantly different from issues of the past. There are two primary mega-issues facing the current era: mega-disasters and megacities. The mega-issues of today are challenging because the currently existing policy is not designed to deal with this magnitude of challenge. Furthermore, other issues facing the current era—such as under-development, ethnic diversity, regime stability, etc.—can only be addressed through collective action and a global perspective. However, this is quite difficult because many of these issues are viewed differently throughout the world. Finally, it is important to be careful when trying to compare different eras in different times. Analysts today are likely biased in thinking that the current era is unique because they are living in it. This era may be unique, but it is not
Panel Four reviewed the role of social sciences in national security as well as validation and validity concepts. Understanding and utilization of social sciences is critical for DOD operations in the 21st century. Social science uses theory to understand intentions and to explain causal links between actions and outcomes. We need an entire spectrum of social science disciplines (economics, sociology, communications, history, etc.) to understand complex problems. From an operational viewpoint, a set of validated social science theories are a good foundation for building a framework capable of informing decision-making. However, social science theories are often not validated for specific military decision- making processes. Thus, it is dangerous for operators to treat a discipline’s theories as fact without first consulting with scientists familiar with the limits of those theories. There is a mismatch between the defense and social science culture. One necessary way to bridge the divide is to train and develop a cadre of military social scientists.
The Feedback from Commands Panel provided an opportunity for representatives from the commands to discuss their pressing needs and key operational requirements. First, all of the commands emphasized the need for greater cooperation within the DOD as well as the whole of government. Building relationships with non-traditional and non-government entities, like those attending the SMA conference today, are increasingly important in a resource constrained environment. USNORTHCOM identified countering threat networks as its primary operational focus. Therefore, it is imperative for DOD to invest in interagency collaboration and provide support to law enforcement partners in combating transnational organized crime. This will provide for a better understanding complex, transdimensional networks. PACOM has the most diverse portfolio of all of the COCOMs; therefore, its requirements range from nuclear deterrence, counterterrorism, geo-political stability, transnational crime, natural disaster response, cyber security, and human trafficking. PACOM’s chief objective is to stay in steady state operations while strengthening relationships with countries in its area of responsibility (AOR). AFRICOM faces multiple challenges as well including terrorism, weak governance, natural resource management, illicit trafficking, humanitarian assistance, training, border security, maritime security, and defense institution building. AFRICOM relies on soft levers of power to address many of these issues. CENTCOM is facing new threats (threat financing, supporting rule of law, etc.) that traditional military forces have not had to face. These threats require a multi-layered solution that relies on cooperation, liaison, and engagement with non-traditional partners. SOCOM’s challenges include an uncertain future, volatile trends, redistribution of power, and the increasing role of non-state actors (NSAs) and transnational criminal organizations (TCOs). Other threatening trends include youth bulges, shifting demographics, and urbanization. Globalization and accelerated change place pressure of the system making the scale of the problem worse. SOCOM will meet its challenges by strengthening its global soft power network. This means increasing the capacity of allies, partners, and the interagency community to respond to the world’s problems. SOUTHCOM’s mission sets include counternarcotics trafficking, counter TCO, and disaster response. SOUTHCOM has always operated with resource constraints. It has developed strong interagency partnerships to compensate.
Panel Five discussed the “new” face of transnational criminal organizations (TCOs). The continually evolving strategic environment, coupled with the ascendant role of TCOs, necessitates a comprehensive understanding of these organizations. TCOs represent a globally networked national security threat and pose a real and present risk to the safety and security of Americans and their partners across the globe. The TCOs of today are profit driven organizations. One of the key challenges in combatting TCOs is to identify the illicit networks and finance organizations that are the oxygen of a TCO. TCOs are sophisticated organizations that are constantly evolving and trying to combat them is becoming more difficult. Often times, legislation does not keep up with the sophistication and evolution of these TCOs and their tactics. It is imperative that legislation continues to evolve as the TCOs become more sophisticated. Furthermore, when combatting TCOs, it is essential that a collaboration effort exist between the defense, intelligence, law enforcement, and other interagency partners. The United States must continue to build the capacity and capabilities of its partners and the interagency community in combatting the TCO threat.
Invited speaker Brig Gen Timothy Fay, JS/J33, noted that during the Feedback from COCOMs panel, none of the representatives mentioned nuclear deterrence, yet it is one area where the DOD needs SMA’s help. One of the biggest challenges of nuclear deterrence is the lack of articulate, informed, rigorous discussion and research. For example, little effort has been applied to understanding the illicit networks that built many of today’s nuclear programs such as that of Pakistan and North Korea. Urban legends—such as that the United States no longer needs or uses its nuclear arsenal—continue to drive the debate. Strategic weapons are made for deterrence, not deployment. We use these weapons every day. They are effective and a part of our adversary’s decision calculus. Another challenge facing the DOD today is how to further adapt policy and strategy in alignment with a smaller arsenal and a more uncertain world environment. SMA has done some great work to contribute to this conversation, but there is a lot more that needs to be done.
Panel Six discussed the sociotechnical world and its new era of disruption and opportunities for innovation. The rapid and continual coevolution of the social and technological sectors is creating a globally pervasive sociotechnical ecosystem. The current security problems facing the United States are social change problems. As a result, it is crucial to understand the full social realm—narratives, networks, interests, identities, vocabularies, desires, and disgusts. Cultural dynamics drive the evolution of technologies as much as the actual technological problem. Connectedness is a new dynamic that is crucial and underpins the current era. Connectedness is what makes mega-issues and mega-events possible. When talking about the framing of problems on a global scale, it is the awareness of the problem that makes it mega, and connectedness increases overall awareness. The operational environment is constantly evolving. The question becomes, how does the United States operate in this changing environment, and what does this change mean for stability? Stability needs to be defined as the ability to adapt to a changing situation. The new status quo is that there is no status quo.
Invited speaker, Lieutenant General Robert E. Schmidle, Jr., USMC, spoke about the intersection of national security and universal principles. He argued that universal principles do not exist; context matters. Some saying the admonition not to kill is a universal principle, but killing to defend oneself is permissible. He further argued that the assumption that rationality guides decision-making is also flawed; man can reason his way through anything. Instead, people rely on hinge beliefs—practices that define a culture. Not knowing or understanding a partner’s or adversary’s hinge beliefs puts one at a disadvantage from the beginning. The search for universal principles is debilitating to our ability to come up with a coherent national security strategy.
Panel Seven examined the importance of understanding megacities in the 21st century. Megacities are rapidly growing and changing population centers where urbanization often far outstrips the ability of governments to enforce rule of law and provide basic socio- economic services such as clean water, sanitation, etc. As a consequence of these deficiencies, these densely populated urban areas can become spawning grounds for public resentment, criminal activity, and political radicalization, which is a national security concern for U.S. policymakers. Understanding megacities is crucial. Urban areas are the key terrain of the future. Developing world megacities thus far have been surprisingly resilient, but the potential for a natural disaster or threat to sovereignty from a non-state actor loom. Megacities are new phenomena and must be understood for future U.S. defense and diplomacy actions. A significant challenge to understanding megacities is the sheer amount of data that is involved in the process of understanding, making interagency collaboration and information sharing key. A method for making sense of all of this data and visualizing it clearly needs to be created. There is a need for a planning support framework for understanding megacities—a model that marries the benefits of rigorous critical thinking with the applied setting in which planners and operators work. A method needs to be developed for fusing these two aspects together to produce a more holistic understanding of megacities.
Panel Eight explored long- and short-term regional and sub-regional stability in South Asia and the Western Pacific region. Panelists argued that the division of South Asia into two COCOM AORs makes it difficult for analysts and planners to address transboundary concerns. Furthermore, analysis must take place at the regional or sub-regional level. India is a rising power, but it is cautious not to be seen as a counterbalance to China. India wants regional balance, participation in the region’s strategic dialogue, and translation of dialogue into actual cooperation. Countries in Asia are concerned about what the future presence of the USG in the region will be given budgetary constraints and China’s aggressiveness in the South China Sea. Countries in Asia will still look to the United States for security, but they will also begin diversifying.
Panel Nine discussed neuroscience and its implications for national security operations. The Brain Research through Advancing Innovative Neurotechnologies (BRAIN) Initiative is a new research effort started by President Obama to revolutionize the understanding of the human brain by accelerating the development and application of innovative technologies. Approximately $100 million will be invested for scientific research during FY 2014 as part of the BRAIN initiative, which will be led by the National Science Foundation (NSF), National Institutes of Health (NIH), and Defense Advanced Research Projects Agency (DARPA). The study of the brain is important because it is the wellspring of human behavior. In the national security domain, especially, there should be an interest in understanding the brain because it is part of the ecology that drives human behavior that is important to national security. Neuroscience allows us to access and engage the brain. This insight into the brain is beneficial for the healthcare, public life, global relations, and public defense realms. It is clear that neuroscience represents a viable science and technology pursuit for the next 10 to 20 years. Areas for growth that need to be developed over this timeframe with respect to understanding the brain include improving the understanding of how the brain recognizes problems, influences culture, and functions in groups.
In conclusion, LTC Matthew Yandura thanked the panelists, moderators, and conference attendees for another successful SMA annual conference. He encouraged participants to build on relationships formed during this conference. There has to be value in relationships or conferences like this go away. The military community should remember that they are not just recipients of this scholarship and research; they are part of the community in service of this nation.
Humans in the Loop: Validation and Validity Concepts in the Social Sciences in the Context of Applied and Operational Settings.
Author | Editor: Cabayan, H. (Joint Staff), Ehlschlaeger, C. (ERDC), McGee, A. (Naval Postgraduate School) & Ackerman, G. (University of Maryland, START).
Threats in the 21st century are increasingly complex, requiring multiple perspectives and disciplines to understand and anticipate challenges. National security issues will require consideration of the insights that might be gained through social science analysis in order to provide broader understanding of both challenges and potential solutions. Many of the challenges and potential missions faced by the Department of Defense (DOD) will be multi-faceted in their most fundamental nature. To better understand these issues, their origins, and potential solutions, we need to think clearly about insights provided about the psychological and social dynamics impacting complex security problems. We can anticipate military operations and missions in a networked, dynamic global environment where modern media, the pace of technological change, and speed of events overlay often long standing historic social legacies and conflicts. We can turn to the social sciences to better understand the intersection of new technologies and legacies and, therefore, assist in crafting strategies to deal with current and emerging issues.
This white paper discusses the validity concepts and validation of the social sciences in the context of applied and operational settings. It focuses on a key issue: How do we gauge the degree to which our frameworks, models, and measures of human social behaviors correspond to the real issues with which DOD operators are concerned? It addresses these issues from several perspectives:
- Scientific Validation in Social Science: What concepts are appropriate for assessing the “goodness” of the social science within the scope of DOD missions?
- Determining Mission Applicability: Social sciences play roles at various phases of military planning. Will these necessitate varying degrees of validation?
- The need to develop military social scientists to bridge the gap between social sciences as an academic discipline and their potential applications in strategic, operational, and tactical decision making.
Whether planning how to help train and develop a military unit, motivate an individual from another culture to participate in an activity, deter a nation-state from a course of action, stabilize a village, or persuade individuals to reject an extremist group, analytical efforts require thinking about the fundamental dynamics of people, groups, and societies. As a result, analysts, planners, and operators need to become more informed and active consumers of social science knowledge. This white paper is aimed at both motivating readers to confront that challenge and at providing some basic insights to reduce the scope of the challenge. Greater engagement with both the body of social science knowledge, and with the process of social science itself, has the potential to increase DOD effectiveness in an increasingly complex, less predictable, more connected, and more problematic world.
Use of the social science techniques in the DOD has a long pedigree. Yet the challenge remains over how to best leverage social science tools to support military operations.
Challenges in assessing reliability and validity of social science tools, techniques, and models, especially those developed for use in Information Operations, include the following.
- Human and social science fields typically lack theoretical maturity as compared with the physical sciences. This challenges the accuracy or representation and the expertise of users.
- Human social behavior often reflects a rich and complex problem space. This challenges the realism of the representation.
- Human social behavior involves many unobservable phenomena. This challenges the expertise of subject matter experts and the credibility of the model to users.
- Both psychological awareness and human behavior involve socially constructed factors and variables. This challenges the accuracy and realism of the representation.
- Consistency in assumptions related to a model’s purpose when reusing scientific statements/theories that are encapsulated in software is essential.
Essentially, validation is about what works and what does not. At the operational level, people want workable tools to current problems. In this context, a “validated” theory has to be relevant to the operations community.
In addition, the white paper highlights the need for a cadre of military social scientists that understand both the academic and operational environments and act as a bridge between these two now very different environments. These individuals should be able to elicit user requirements and then employ their domain knowledge to satisfy those requirements. Therefore, there is a need develop a strategy as to how to best provide a focused, comprehensive, and integrated social science training program for officers and enlisted that spans their entire career.
The past decade of combat has once again brought the “human domain” of warfare front and center. The classic geographic factors of physical, cultural, economic, and political have demanded attention from the strategic to tactical level of range of military operations. Operational requirements have historically inspired innovation in organizations and diversification in cross-sector collaboration. This legacy can be used as a foundation for the growth of “military social science.”
The essential concern of the social sciences is human behavior. The classic disciplines (e.g., economics, political science, sociology, anthropology, etc.) loosely align with the levels— individual, group, societal—and the subjects of those behaviors. What social scientists do is attempt to describe and explain the influences and interactions among complex sets of factors that span human behaviors. This white paper continues the SMA White Paper series, The Role of the Social Sciences in DOD Mission Analysis and Planning, with a discussion of validity concepts and validation in the context of applied and operational settings. In so doing, it focuses on a key issue, namely: How do we gauge the degree to which our frameworks, models, and measures of human social behavior correspond to the real issues with which DOD operators are concerned?
Contributing Authors
Mr. Gary Ackerman (START, Univ. of MD); Mr. Ricardo Arias (SOUTHCOM); Dr. Allison Astorino-Courtois (NSI); Lt Col Alexander Barelka (USAF AFMC); Mr. David Browne (PACOM); Dr. Charles Ehlschlaeger (ERDC); Dr. Dana Eyre (SoSA); Ms. Laurie Fenstermacher (AFRL); Mr. Ben Jordan (TRADOC/G-2); Dr. Anne McGee (NPS); Ms. Jane Peplaw (SOUTHCOM); Mr. Eric Ruenes (DIA); Dr. Laura Steckman (PACOM); Dr. Ivan Welch (TRADOC/G-2) Editors: Dr. Hriar Cabayan (JS/J39); Dr. Charles Ehlschlaeger (ERDC); Dr. Anne McGee (NPS); Mr. Gary Ackerman (START, Univ. of MD)

Operational Relevance of Behavioral & Social Science to DOD Missions.
Author | Editor: Canna, S. (NSI, Inc).
This paper emerged from the “A World in Transformation: Challenges and Opportunities” Strategic Multi-layer Assessment (SMA) Conference in November 2012.2 Leaders from across the USG addressed the emerging challenges of the 21st century for defense analysts, planners, and operators. The first decade of the 21st century has ushered in a period of rapid change across the globe: demographic upheavals are challenging the status quo, classic nation states are in decline, and people are more interconnected than ever. Panelists agreed that in this uncertain environment, the social sciences3 play an ever-expanding role. Thought leaders from across the defense community discuss the relevance of social science to DOD operations in this section.
Building Frameworks to Inform Whole of Government Response
Maj. Gen. John “Jack” Shanahan, Deputy Director for Global Operations, Operations Directorate, Joint Staff
A paradigm shift is occurring across the globe. We do not yet know how the world will look when this shift is completed, though it is already being characterized within the Interagency as the “new normal.” We must consider two paradigms. First, adversaries and potential adversaries—often grouped under the rubric of Violent Extremist Organizations, or VEOs,– are becoming syndicated in ways we did not fully anticipate or appreciate a decade ago. We are witnessing a rising trajectory of communication, collaboration, and sharing of ideas, weapons, lessons learned, and tactics among disparate VEOs that once seemed to have very few common interests or goals—or even if they did, they were unable to join forces in ways that represented a more significant threat than they did in isolation. VEO cooperation, coordination, and synchronization are enabled by the explosion of social media and almost- instant global communications. At the same time, we are not keeping up with this VEO paradigm shift; when we do, it is often in a predominantly tactical and reactive manner. In short, our adversaries and potential adversaries are more rapidly and effectively shifting paradigms than we are.
There is an unmistakable ideological component to this paradigm shift. We are in danger of losing the strategic narrative, the so-called ‘battle for ideas.’ Our adversaries and potential adversaries are engaged as never before in a competition for the ideological high ground. Distorted ideas and ideals that were easily brushed aside twenty years ago are finding an unprecedented audience and gaining a dangerous foothold in the ungoverned spaces of the science can and must play a central role in both understanding and competing against the VEO ideology. In today’s information environment, the Internet and social media are among the most potent weapons in the VEO arsenal. We must engage readily and continuously in this electronic battlespace or we will lose the clash of ideas.
Federal agencies are working to respond to a broad spectrum of complex social threats facing the United States in the 21st century including radicalization, cyber radicalization, instability, and insurgency, but there is no uniformity of approach. The social sciences can provide a rigorous framework to explain these phenomena and to guide research, analysis, and operations. Social science knowledge, methodologies, and models inform the commanders so that conflict stays left of boom. However, further research is needed and operators need to better understand the role and potential of social science to inform decision-making and to ensure our paradigm shift is as substantial and as enduring as that of the VEOs.
Responding to Emerging Threats
Mr. Earl Wyatt, Deputy Assistant Secretary of Defense, Rapid Fielding in the Office of the Assistant Secretary of Defense for Research & Engineering
One of the Rapid Fielding Directorate’s (RFD) missions is to respond to emerging threats by identifying, developing, demonstrating, assessing, and rapidly fielding innovative concepts and technologies to meet operational needs. The social sciences are uniquely positioned to contribute knowledge, tools, and models to address some of the most pressing questions facing operators and decision makers today including:
- How do we best anticipate and disrupt the triggers of violent actions?
- How do we prepare for the unintended consequences that may result from U.S. engagement?
- How do we communicate U.S. intentions and foster trust in a country with decentralized government?
- How can we defuse the need for kinetic engagement and measure the success of these efforts?
- How do we best strengthen and measure the benefits of building partner capacity?
To address these questions, we need social science models capable of scaling up or down to address a wide range of divergent threats. This is critical to establishing a leaner, more agile force to effectively operate across all domains. It is imperative that the delivery of these technical capabilities is accelerated to win the current fight.
Multidisciplinary Responses to Complex Challenges
Mr. Ben Riley, Principal Deputy, Deputy Assistant Secretary of Defense for Rapid Fielding in the Office of the Assistant Secretary of Defense, Research and Engineering
Threats in the 21st century are increasingly complex and require multiple perspectives and disciplines to understand and anticipate challenges. No longer can the DOD rely solely on subject matter experts to understand and engage with populations. The social sciences need to be deployed at the tactical level. Social science insights, theories, and models give the commander the kind of information that is critical for him to achieve his mission in complex environments. However, it is not enough to employ social science tools and methods in the operational environment. The tools require the intellectual curiosity of the commander in the fields. The community needs to concurrently invest in training officers how to employ social science tools and methods.
The Changing Role of Social Sciences in the DOD
Dr. Robie Samanta Roy, Professional Staff Member, Senate Armed Services Committee
The changing nature of warfare emphasizes the need to develop a deeper understanding of the human perspective. Conflict is emerging in diverse corners of the world, and the DOD needs to develop the expertise in each of these regions. Social science initiatives are crucial for understanding this human terrain.
However, investment in the social sciences faces a few obstacles. First, the gap between the research and user communities needs to be bridged and narrowed. Second, coordination within the research community needs to be improved to eliminate redundancy, focus on meeting warfighter needs, and quickly transition from basic to applied research. Third, the emphasis on multidisciplinary approaches must be maintained and further developed including bringing together experts from across a broad spectrum of disciplines. Fourth, the community needs to do a better job of developing measures of effectiveness (MOE) to understand the impact of operations on communities of interest. Finally, the community needs to address the verification and validation of high quality data, models, and theories.
It is necessary to shape the future direction of social science programs now. This shaping will include the training of future experts to ensure that these efforts are sustainable. Additionally, through increases in international cooperation, greater insight on “the other” will be gained. Furthermore, research into the role of political and religious ideologies needs to be pursued. Finally, the convergence of behavioral science and neurobiology will help inform future challenges including how best to respond to adversaries that do not have the same ethical constraints that the U.S. does.
Contributing Authors
Maj. Gen. John Shanahan (Joint Staff), Mr. Earl Wyatt (RFD/ASD R&E), Mr. Ben Riley (RFD/ASD R&E), Dr. Robie Samanta Roy (SASC), Hriar Cabayan (SMA OSD), David Adesnik (IDA), Chandler Armstrong (USACE ERDC), Allison Astorino-Courtois (NSI), Lt Col Alexander Barelka (USAF AFMC), Thomas Bozada (USACE ERDC), David Browne (PACOM), Charles Ehlschlaeger (USACE ERDC), Dana Eyre (SoSa), LTG Michael Flynn (DIA), LTC John Ferrell (SOUTHCOM), LeAnne Howard (SOCOM J5), Robert Jones (SOCOM J5), David Krooks (USACE ERDC), Anne McGee (NPS), Timothy Perkins (USACE ERDC), Dan Plafcan (OUSDI), Lucy Whalley (USACE ERDC)
Insights from Neurobiology & Neuropsychology on Influence and Extremism—An Operational Perspective.
Author | Editor: Reynolds, M. (Joint Staff) & Lyle, D. (USAF).
This report provides the operational and policy communities with a deeper understanding of the unique behavioral and neurobiological factors that underlie political extremism enhanced by interaction in the cyber realm. It addresses the implications of advances in neurobiology and neuropsychology for the way we plan and execute military operations as part of a comprehensive approach to counter violent extremists and the spread of their violent political narratives. The paper focuses on the intersection of emerging cyber technologies and human biology including of both psychological and neurobiological dimensions of behavior. For the purposes of this white paper, we will refer to these two dimensions as cyberpsychology and cyberneurobiology respectively.
Key Insights
- Modern information technology is empowering violent extremist organizations (VEOs) by providing cheap and anonymous forums to target large audiences. Advances in Cyber- Based Communication Technology (CBCT) will revolutionize how the DOD operates in cyberspace and will heighten challenges to Military Information Support Operations or MISO (formerly psychological operations or PSYOP).
- The next twenty years will see a paradigm shift in the fundamental character of the Internet that will revolutionize how people interact globally. Changes include
- the shift from Internet Protocol version four (IPv4) to Internet Protocol version six (IPv6) and the emergence of the Next Generation Internet;
- alternative Domain Name Systems;
- generic top-level and internationalized domain names;
- Broadband mobility;
- Cloud computing and big data;
- Ubiquitous computing; and
- IPTV (a technology that allows for broadcast of audio-video material).
- Bottom line: The impending changes will add additional challenges to the ability of MISO and cyber operations to influence perceptions.
- The next twenty years will see a paradigm shift in the fundamental character of the Internet that will revolutionize how people interact globally. Changes include
- Communication technologies are means, not ends—they shape social worlds by connecting people in distinct ways, but it is the social world itself that creates outcomes.
- Deemphasizing the distinction between mass media and social media facilitates more fruitful exploration of the social implications of different means of communication.
- A four-way communication typology (i.e., speed, directionality, span, and configuration) allows exploration of the human terrain.
- CBCT can blur the lines between physical reality and cyber-formed reality, which may differ in delivering catalysts for extremist action while potentially removing vital inhibitors.
- CBCT likely does not contribute to radicalization and mobilization to political extremism in a linear fashion. Rather, the various modes of CBCT interact with shaping factors (i.e., culture, values, genetic background, access to technology, etc…) and transition factors (i.e., activators, catalysts, inhibitors, and interventions) to produce psychological and behavioral outcomes.
- Only a very small subset of individuals becomes more radical in their thinking or mobilizes due to interactions with CBCT.
- The impact of CBCT on a person is dependent on the individual’s motivation for using the medium.
- Bottom line: CBCT often provides isolated individuals the informational equivalent of an echo chamber through which they can actively or passively access information that is consistently biased toward already expressed preferences and, thus, reinforces and strengthens their existing worldviews and limits the probability of their encountering information that is potentially contradictory or disconfirming. Tailored search algorithms and the psychologically rewarding behavior of participating in “echo-chambers” accentuate these tendencies.
- Complex systems concepts provide theoretical frameworks and insights important to designing tailored counter violent extremist organizations (VEO) intervention strategies.
- Neurobiological underpinnings, processes of socialization, and the constantly changing modern information environment help illuminate the causes for the bottom up emergence of VEOs. In so doing, they help suggest operational approaches to defeat them.
- Socialization has always required communication. The rapid expansion in digital media dramatically increases the ways that social groups can form, organize, and plan for action.
- Connectedness in the modern information environment tends to reinforce, not replace, basic human needs to connect with others in person.
- Real complex systems do not resemble static structures to be collapsed; they are usually much closer to flexible, constantly respun spider webs.
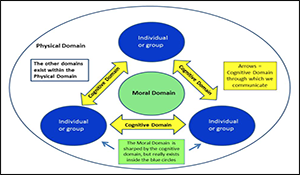
- Countering strategies should focus on the interaction of the physical, mental, and moral domains instead of physically focused, relatively static center of gravity concepts.
- Without an understanding of how all three domains relate to one another dynamically, one may miss the right points of leverage and combinations of interventions that will produce the greatest synergetic effect to influence the direction and momentum of constantly evolving social systems.
- Bottom line: A strategy based on a solid understanding of the dynamic linkages between all three social domains (physical, cognitive, and moral), coupled with solid comprehension of complexity concepts like bottom up emergence, is more likely to help us choose the right combinations of interventions to successfully derail radicalization before violent ideas become violent acts and before violence becomes part of the unquestionable core identity of the individual and the group.
- Emerging research in cyberpsychology and cyberneurobiology can be integrated with existing PSYOP/MISO processes to create both a set of individualized influence tactics and guide their implementation.
- Synthesizing traditional methods with recent advances in neuroscience, cyberpsychology, and captology (the study of persuasive technology) can produce an advanced set of personalized persuasion tactics. This would allow PSYOP/MISO planners to rely on firmly established linkages between perception and actions when developing both their intelligence requirements and the desired psychological effects.
- Research in cyberpsychology and cyberneurobiology should produce empirically informed processes designed to target underlying neural mechanisms to create specific psychological effects on a target.
- Countering VEOs must address target audiences at the macro (population) and micro (individual) levels.
- Bottom line: Appending existing processes to include experimental findings in cyberpsychology and cyberneurobiology along with technological advances from captology will allow the U.S. to combat radicalization across domains with greater precision. Currently, however, there is insufficient empirical data to support explicit linkages between triggers and specific behaviors, and thus experimental validation is necessary.
Selected Chapters:
- Cyber on the Brain: The Effects of Cyberneurobiology & Cyberpsychology on Political Extremism (A. Desjardins)
Contributing Authors
Maj Gen John Shanahan (Joint Staff), Col Marty Reynolds (JS/J-3/DDGO), Lt Col David Lyle (USAF), Ms. Abigail Desjardins (NSI), Maj Dave Blair (Georgetown University), Maj Jason Spitaletta (USMCR), Dr. Panayotis A. Yannakogeorgos (Air Force Research Institute), Dr. Hriar Cabayan (OSD
Topics in the Neurobiology of Aggression: Implications to Deterrence.
Author | Editor: DiEuliis, D. (HHS) & Cabayan, H. (Joint Staff).
This paper provides a series of selected topics on the neurobiological basis of aggression, in the interest of introducing this field of science to the community of experts in deterrence. Thus the topics covered are those of most relevance to inform a deterrence community of how neurobiological considerations may be incorporated as potentially useful tools in deterrence practice. The material is presented in 3 Parts: A summary of the basic neurobiology, a few chapters on behavioral impacts of that neurobiology, and finally a “systems summary” that integrates these issues for readers. Topics include the role of genes and environment, group vs. individual aggressive behaviors, the role of trust and altruism, reward/punishment, and premeditated vs. impulsive aggression, among others. The paper also discusses the continuum of scientific evidence base, from the basic neurobiology of reactive aggression, to pre- meditated aggression and what connections can be understood and conjoined to the psychological and behavioral evidence base.
Key insights provided by contributing authors to this white volume that are of particular relevance to the operational community include:
- It is not possible to understand the biology of behavior without understanding the context in which that biology occurs, as well as the society in which that individual dwells. This is true in our understanding of aggression; there is no highly accurate means of identifying individuals likely to commit an impulsive or planned violent act. The context in which aggression and violence occur can be modified much more easily than identifying individuals likely to commit aggressive act; by manipulating context, society may reduce aggression by individuals indirectly.
- Much aggression is motivated by conflict between in-groups and out-groups. An understanding of genetic and environmental factors can elucidate pathways toward aggression and begin to explain how various environmental factors such as media, propaganda, or informal mechanisms of narrative messaging, can be used to manipulate the neurobiological mechanisms that inform the psychological architecture of susceptible individuals. In that context, foreign policies which overtly impose governance or values alien to local cultures, may constitute provocations to violence.
- Within groups, punishment and reward cannot be understood outside the context of cooperation. Cooperation is stable when defectors can be identified, excluded and/or punished, and when prospective cooperators can be identified, engaged, and rewarded through cooperative exchange. Research indicates reward may function less effectively as a behavior-changing strategy, but may function more effectively as a behavior- sustaining strategy.
- Punishment in the context of group conflict cannot be understood absent the evolutionary logic of warfare between groups in an ancestral environment that was “offense dominant”. The “secure retaliatory force” that nuclear strategists argue is necessary for equilibrium in the nuclear age is nothing but a euphemism for “guaranteed vengeance,” in which states promise a punishment that is greater than the benefits of striking first.
- States where the rule of law is weak can beget societies characterized by “culture of honor” traditions, in which, in the absence of capable and legitimate third-party enforcement, reputation for disproportionate retaliation/punishment becomes the most effective safeguard against personal violence.
- Deterrence as a concept may be a long-learned part of our psychology. Because challenges, predators, or out-group threat have faced humans for millennia, analyzing the notion of deterrence from the perspective of evolutionary models may prove helpful. Rational actors have an interest in settling things with threats but without the use of violence. Vengeance is certain to be provoked by an attack, deterrence kicks in when the initiators cannot be absolutely sure that they’ll be successful.
- Neuroscientific studies of human behavior suggest aggression is a useful but costly strategy and people have a tendency to cooperate in many situations. This has been shown to be chemically regulated, and cooperative behaviors are just as “natural” as aggressive ones. The “Golden Rule” exists in every culture and reveals our essential social nature; this is naturally threatened in situations of threat or high stress.
- Neuroscience and technology offer a viable and potential value of in programs of national security, intelligence and defense. However this will necessitate an acknowledgement of the actual capabilities and limitations of the neuroS/T used – and importantly the ethico-legal issues generated by apt or inapt use, or blatant abuse.
- Context is critically important to our understanding of human behavior and biology is only part of what makes up our human selves and defines us as persons. An integrated approach, one that takes into account the influence of the empirical sciences as well as a social psychological framework, gives us the most holistic understanding of human behavior and produce the greatest improvement in our understanding of terrorism.
Topic Overview
In his introduction, Robert Sapolsky defines “aggression” in the fullest sense as harming, attempts to harming, and thoughts about harming. Two brain regions dominate this. The first is the amygdala, an ancient structure in the “limbic system” (the “emotional” part of the brain). The second is the frontal cortex (FC). It is more complex in humans than in other species, is the most recently evolved part of our brain, and is the last to fully mature (remarkably, in the mid- 20s). There are tremendous individual differences in FC function among people; many of differences arise from differing early life experiences. The limbic system/FC contrast can, in a thoroughly simplistic way, be thought of as a contrast between emotion and thought. A key issue is that genes have far less to do with aggression than is often assumed; genes are not about inevitability, rather, they are about proclivities. In conclusion, Professor Sapolsky states that amid this emphasis on biology, ultimately, it is not possible to understand the biology of behavior without understanding the circumstances of the individual in which that biology occurs, as well as the society in which that individual dwells.
In Part 1 (Aggression and the Brain), Allen Siegel discusses the two forms of aggressive behavior: predatory or premeditated aggression and affective or impulsive aggression. He points out that it is often difficult to detect any response patterns that could be used to predict the onset of predatory aggression – the behavior occurs with no perceived threat, is purposeful and planned, and appears to be devoid of conscious awareness of emotion.
Jordan Grafman and Pamela Blake provide further insights into the aggressive brain. They focus on laboratory work examining the key brain regions involved in impulsive aggressive behavior and control, the types of environmental exposures that could influence aggressive behavior, and the interaction of genetic predisposition, brain damage, and aggressive behavior. They report that specific brain lesions can affect impulsive aggressive behavior, and genetic predisposition can affect aggression as long as the key brain area mediating that effect is not damaged. There is no guarantee of accurately identifying people likely to commit an impulsive or planned violent act, rather, the context in which aggression and violence occur can be modified much more easily than identifying individuals likely to commit aggressive acts. By manipulating context, society can reduce aggression by individuals indirectly.
Peter Hatemi and Rose McDermott point out that much aggression is motivated by conflict between in-groups and out-groups. Aligned with other authors in this white paper, they note that studies of genetic and environmental characteristics can elucidate pathways of aggression. They can provide insights into how various environmental factors, such as the media, propaganda, and informal mechanisms of narrative messaging, can be used by ourselves, allies and adversaries to manipulate the neurobiological mechanisms that inform the psychological architecture of susceptible individuals. From this perspective, US interests may be better protected through the development of strategies to manipulate environmental triggers, and creation of interventions to address the human psychological architecture that responds to threat with aggression. Lastly, provocation is important in potentiating violence. Foreign policies which try to impose governments, institutions, or values alien to local cultures, are likely to be understood as constituting such provocations.
In Part II, some implications of aggressive behavior are presented. Anthony Lopez discusses the human psychology of reward and punishment in light of evolutionary pressures, and in the context of both in-group and out-group behavior. Within groups, punishment and reward cannot be understood outside the context of cooperation. Cooperation is stable when defectors can be identified, excluded and/or punished, and when prospective cooperators can be identified, engaged, and rewarded through cooperative exchange. Empirical data indicates that when punishment is available, cooperation is often stable and free-riding is deterred. Although research on the role of reward in promoting cooperation is relatively lacking, there are indications that reward may function less effectively as a behavior-changing strategy, but may function more effectively as a behavior-sustaining strategy. Punishment between individuals and groups takes the form of a withdrawal of benefits or the conferral of costs. Punishment in the context of group conflict cannot be understood absent the evolutionary logic of group warfare. Evolutionarily, warfare has most often taken the form of lethal raiding and it has occurred in an ancestral environment that was “offense dominant”. Lopez notes that the “secure retaliatory force” (touted by nuclear strategists as necessary for equilibrium in the nuclear age) is actually a euphemism for “guaranteed vengeance,” in which states promise a punishment that is greater than the benefits of striking first. States with weak rule of law beget societies characterized by “culture of honor” traditions, in which, in the absence of capable and legitimate third-party enforcement, reputation for disproportionate retaliation/punishment becomes the most effective safeguard against personal violence.
Rose McDermott and Peter Hatemi provide further insights into the role of emotion in decision making around violence. By exploring the foundations of human psychological and neurobiologically informed notions of threat and deterrence, we can begin to leverage our own biology in service of our very survival through recognition of those environmental cues and triggers which both instigate and extinguish our desires for aggression and cooperation. They discuss two key topics relevant to the theory of deterrence; namely the “Psychology of first strike, Coalitionary Humans, and Maximum Response” and “Leadership and Group Dynamics”. Following similar arguments advanced by Anthony Lopez, they argue that before nuclear weapons appeared, deterrence as a concept was naturally built into our psychology. Because humans have faced challenges, predation, and out-group threats for millennia, analyzing the notion of deterrence from the perspective of evolutionary models may prove useful; examining the genetic and biological mechanisms which precipitate our recognition and response to threat can inform our understanding of how to create more accurate signals and more effective responses. Rational actors may negotiate by using threats, without the use of violence. Where vengeance is certain to be provoked by an attack, deterrence kicks in when the initiators cannot be absolutely sure that they’ll be successful. The section on “Leadership and Group Dynamics” provides reasoning that evolutionary and neurobiological perspectives have served to enlighten aspects of leadership beyond that of traditional models. They propose that a more neurobiologically informed understanding of individual dispositions and personal psychology may reveal triggers that cue a particular individual to respond in a hostile as opposed to conciliatory manner in the face of threat.
In the last chapter in Part II, Paul Zak focuses on the role of hormones on the reduction of aggression. Episodes of aggression, especially repeated aggression by the same individual, are due to combinations of, and interactions between, genes, brains, history, and environments. Neuroscientific studies of human behavior suggest aggression is a useful but costly strategy and most people have a strong bias to cooperate in many situations. Zak demonstrates this is affected by the neuroactive hormone oxytocin (OT). OT appears to function as a chemical regulator that mediates prosocial behaviors by signaling that another person is safe or familiar, even if the other person is a stranger. One can make the case that cooperative behaviors are just as “natural” as aggressive ones, that cooperation with strangers is a typical human behavior, and that conflict among strangers may not be the norm. He reports that laboratory “trust games” capture, in an objective way, the notion of the Golden Rule: if you are nice to me, I’ll be nice to you. Of hundreds of people tested in a variety of cultures, roughly 95% of individuals reciprocate trust. The Golden Rule exists in every culture on the planet and reveals our essential social nature. It appears that OT is largely responsible for reciprocation by sending a safety signal motivating nice with nice. He goes on to point out the role of the environment and states that high stress can inhibit OT and put us into solitary or socially narrow survival mode. Environments that are unsafe, new, competitive, aggressive, or unpredictable induce greater release of certain hormones and thereby inhibit prosocial behaviors, especially such behaviors towards strangers.
In Part III, James Giordano shifts focus towards weaving the basics of neuroscience and technology (“neuroS/T”) into social and cognitive aspects, creating a systems understanding. In a paper entitled “Toward a Systems Continuum: On the Use of Neuroscience and Neurotechnology to Assess and Affect Aggression, Cognition and Behavior” he argues that neuroscience has assumed a prominent role in shaping views of the human being, human condition, and human relationships. Neuroscientific discoveries continue to challenge and promote a re-examination of socially-defined ontologies, values, conventions, norms and mores, and the ethico-legal notions of individual and social good. As a potential analogous framework for “neurodeterrence” he introduces the concept of neuroecology – the study individuals’ neural systems, embedded in groups and environment(s) framed by time, place, culture and circumstance. Defining the neural bases of such biological-environmental interactions may yield important information about factors that dispose and foster various actions – including cooperation, conflict, aggression and violence. This emphasizes the viability and potential value of neuroS/T in programs of national security, intelligence and defense (NSID). He reiterates that any consideration of the possible use of neuroS/T for NSID would require acknowledgement of the actual capabilities and limitations of the neuroS/T used – and importantly, the ethico-legal issues generated by apt or inapt use, or blatant abuse. Otherwise there is a real risk that neuroscientific outcomes and information may be misperceived, and misused to wage arguments that are inappropriate or fallacious. He questions whether ethico- legal systems are in place and realistic and mature enough to guide, direct and govern such possible use and/or non-use. He goes on to state there is the need to develop stringent technical and ethico-legal guidelines and standards for such use of neuroS/T. He advocates a dedication to both ongoing neuroS/T research, and full content ethico-legal address, analyses and articulation of the ways that these approaches may be used, misused and/or abused in contexts of national security, intelligence and defense.
Neuroscience and technology offer a viable and potential value of in programs of national security, intelligence and defense. However this will necessitate an acknowledgement of the
actual capabilities and limitations of the neuroS/T used – and importantly the ethico-legal issues generated by apt or inapt use, or blatant abuse.
LtGen Robert Schmidle (USMC) in his closing editorial comment chapter entitled “An Integrated Approach to Understanding Human Behavior” proposes some final ideas in line with other contributors to this white volume. He stresses that context is critically important to our understanding of human behavior, and biology is only part of what makes up our human selves and defines us as persons living in a given society and culture. He discusses the terrorist as a behavioral example of purposeful aggression and violence. He advocates an integrated approach, one that takes into account the influence of the empirical sciences as well as a social psychological framework, gives us the most holistic understanding of human behavior. He stresses the need to develop a conceptual framework within which to conduct empirical investigations that includes the relevant cultural and historical context. In this instance, both kinds of knowledge, scientific, (i.e. empirical) and philosophic, (i.e. conceptual) are necessary for our understanding of human actions. He concludes by stating that while we may not ever definitively answer the question of responsibility for the development of a terrorist, for example, an integrated approach that takes into account both biology and psychology will produce the greatest improvement in our understanding of terrorism.
Contributing Authors
Robert Sapolsky, Stanford U; John Gunn, Stanford U.; Cynthia Fry Gunn, Stanford U., Allan Siegel, New Jersey Medical School; Jordan Grafman, Rehabilitation Institute of Chicago; Pamela Blake, MemorialHermann Northwest Hospital; Peter Hatemi, Penn State; Rose McDermott, Brown U; Anthony Lopez, Washington State U; Paul Zak, Claremont Graduate U; James Giordano, Georgetown U Medical Center; Roland Benedikter, Stanford U; LtGEN Robert Schmidle, USMC

Over a Decade Later…What Now? What Next? A Multi-Layer Assessment of Terrorism in its Current and Future Manifestation
Author | Editor: Cabayan, H. (Joint Staff), Astorino-Courtois, A. (NSI, Inc), Yandura, M., Sitterle, V. (Georgia Tech), Canna, S. & Popp, G. (NSI, Inc).
This report marries contemporary social science theory, applied research, and operational experience to provide a range of perspectives on terrorism to challenge the reader to ask better, more relevant questions.
This white paper is a follow-on report to a recent publication entitled “Over a Decade Later…What Now? What Next? A Multi-Layer Assessment of Terrorism in its Current and Future Manifestation.” 2 The previous paper was primarily an analytical product intended to provide insight into what current social science research and over a decade of practical experience suggest regarding the most effective counterterror strategies. It was based on comments made during multiple, semi-structured telephone interview sessions conducted between 06 May and 12 June 2013. The current white paper includes a series of articles by authors who participated in the previous white paper. These articles expand on the main themes raised in the previous report and cover topics ranging from strategic and adaptive considerations of terrorism to analytical considerations.
The various contributors to this volume advance insights that are summarized below:
- There is a body of research relating the strategic application of systems thinking, complexity theory, and complex adaptive systems theory to strategic planning in business and a variety of organizational constructs. These have implications in the deliberate planning of regional and global strategies and, critically, to our current counterterrorism strategy.
- We frequently seek clarity by way of attributing political or particular ideological reasons and affiliations behind terror acts when such attribution is really viewing the present and future through the lens of the past. Looking forward, real resilience requires having a narrative of our own that projects a purpose beyond responding to adversity. Furthermore, we will continue to be perplexed by the enemy in our counterterrorism strategy as long as we are unclear as to our own purpose and direction.
- The convergence of rapidly advancing scientific sectors (biotech, nanotech, energy, materials, etc.) combined with the availability of CBCT (Cyber-Based Communication Technology) could produce an entirely new generation of threat capabilities. The evolving socio-technical ecosystem is transforming temporal and spatial characteristics from individual to trans-State behaviors, simultaneously creating new paradigms for emergence and support of terror activities on a global scale.
- As terrorism adapts to the market place, we need to move from “terrorist” towards an understanding of market entry and risk mitigation. The “cost” of terror and of counterterror activities is an increasingly important perspective. Turning the lens on ourselves, we need to ask what it will take to compete, to grow, and to expand our own market share, and re-establish our national identity as a global consumer brand of choice.
- There is a need for much better psychosocial intelligence on foreign public opinion regarding key issues. Open-source intelligence can be used to provide such intelligence for counterterrorism. Findings from on-going efforts highlight the importance of testing theories and hypotheses about the bases of terrorism and political violence with statistical data on people’s attitudes, beliefs, sentiments, and other characteristics.
- Thematic Content Analysis (TCA) of activist, militant, and terrorist groups has demonstrated the usefulness of such analyses to assess groups’ acceptance of, and proneness to, violence. An approach based on this concept and using measures of integrative cognitive complexity from discourse analysis has been operationalized and proven successful for primary prevention. Efforts are underway for deploying this capability on the Internet.
- Lone-actor terrorists have been relatively rare thus far. They may, however, exhibit personality and social traits that would support a useful profile, unlike group-based terrorists who vary in a myriad of ways. Recent research suggests two possible profiles of lone-actor terrorists: the disconnected-disordered and caring-compelled profiles.
- Similarly, there is presently no empirically based psychological or demographic profile of individuals that perpetrate terrorist acts indicating a predisposition toward joining violent extremist organizations. Based on what limited empirical evidence is available, however, a set of individual psychological risk factors for individual radicalization may be proposed. While more study is needed before these may be established as firm indicators, these individual-level attributes may provide a starting point toward profiling individual willingness to participate in or perpetrate political violence.
- There are a myriad of theories and frameworks to explain why and how individuals may radicalize to violence, and many shortcomings remain that limit the validity and generalizability of the findings. Advances in qualitative methodologies offer a framework for improving the understanding of the complexity inherent in the phenomena of radicalization and non- radicalization. Improved understanding of the multiple potential pathways into radicalism and terrorism should lead to better-tailored CVE (countering violent extremism) policies that are more effective and efficient.
- There is a need to build teams—Joint and Interagency (and community) partners—to understand the information that comes from complex environments in order to organize counterterror practices in ways that inform and influence the behavior of friends and adversaries.
Brief Topic Overviews
Rethinking Counterterrorism: The Need for Systemic Strategic Planning and a Strategic Campaign to Address Violent Islamist Extremism that Manifests Itself in Terrorist Acts–CAPT Wayne Porter (NPS): There is a body of research related to strategic planning in an uncertain and dynamic environment. This research includes, among other topics, analyses of the strategic planning and thinking process, organizations and strategic change, multi-national corporation strategic planning in times of turbulence and uncertainty, backcasting for strategic planning of sustainable development, cognitive biases on strategic planning, and sensemaking in the boundaries of stability and instability, order and chaos. Further research is needed, though, in analyzing the potential benefit of employing methods of system thinking and complexity in the deliberate planning of regional and global strategies. Critically, this applies to our current counterterrorism strategy and the phenomenon of ideologically based violent extremism. While this paper focuses primarily on radical Islamist extremism, the concepts discussed apply equally to any ideologically based extremist network seeking to employ terrorism.
War on Terror or a Search for Meaning?—Dr. Bill Durodié, Professor & Program Head, Conflict Analysis & Management Programs, School of Humanitarian Studies, Royal Roads University: The events of 9/11 necessitated a response. What shape that took was determined by the meaning attributed to those events, in its turn influenced by the mood of the times. Unfortunately, these latter elements reflected the sense of confusion that gripped the West in the aftermath of the Cold War. This paper argues that we will continue to be perplexed by the enemy in the war on terror so long as we are unclear as to our own purpose and direction. Indeed, the perpetrators of such acts today appear more influenced by Western dystopianism than Eastern mysticism. Real resilience requires having a narrative of our own that projects a purpose beyond responding to adversity.
Technology, Society, and the Adaptive Nature of Terrorism: Implications for Counterterror–Dr. Valerie Sitterle (Georgia Tech), Dr. Rodrigo Nieto-Gomez (NPS), Maj David Blair (Harvard University): As technology continues to advance and increasingly permeate society, generating violence that makes a societal group feel vulnerable is not difficult. Generating the desired interpretation of that violence is hard, however, and is critical to the coupling we need between future U.S. counterterrorism (CT) and information operations (IO) strategy. This latter space, with all of its socio-technical nuances, is where threats we classify as “terrorists” have excelled. This paper will begin by explaining the nature and importance of socio-technical complexity and its relevance to terroristic adaptation. A true socio- technical confluence perspective, distinct from the traditional view that treats the dimensions as distinct elements that happen to coexist, promotes awareness of active and passive influences that exist bi- directionally between the social and technological elements. The cyber realm then becomes both a means through which terroristic attacks are conducted or directly targeted and an ecosystem. In this latter view, individual and community (up to state and even trans-state) patterns of organization are transformed via completely new paradigms across temporal and spatial scales of communication and information sharing across societal sectors. This has significant ramifications for emergence of terror cells, their coordination, and passive support of their activities in a global scale. Behavior of terror cells in this complex environment may be more intuitively understood from an entrepreneurial business model analogy, which naturally expands into a consideration of the multiple dimensions associated with both conducting terror and striving to build protective measures against it. Since adaptation is a hallmark of living systems, the U.S. cannot stifle innovative advances by a terroristic adversary through reliance on a static U.S. counterterror strategy. Rather, the U.S. must lead disruptive innovation in order to drive strategic surprise and strain the capacity of these threat groups to adapt.
Market Economies and the Collision of Narratives…Approaching Terrorism Through Branding and Marketing Methodologies–Mr. Scott Kesterson, Asymmetric Warfare Group: Terrorism has become a global franchised business, and, in terms of brands, al-Qa’ida (AQ) is king. Their brand has come to guarantee global positioning, brand name recognition, easy recruiting, as well as abundant financial resourcing. With the loss of Osama bin Laden, however, al-Qa’ida’s brand supremacy is now vulnerable to new tiers of competition; their brand that could have been characterized by adaptability, innovation, and persistence has suffered a loss of consumer confidence. As terrorism adapts to the market place, our conversations need to move from “terrorist” towards an understanding of market entry, branding, and risk mitigation. What are the market factors that create brand durability for terrorism? What are the value propositions that these markets are responding to? What are the market elements that allow for growth and the ability to franchise? Turning the lens on ourselves, we then need to ask what it will take to compete, to grow, and to expand our own market share and re-establish our national identity as a global consumer brand of choice.
Counterterrorism and Muslim Public Opinion–Dr. David R. Mandel (DRDC Toronto): A widely shared view is that counterterrorism must address the psychosocial and cultural aspects of Islamic violent extremism if it is to succeed strategically. Another is that we need much better psychosocial intelligence (what might be called PSYINT) on Muslim public opinion regarding key issues. In this paper, the author draws on open source polling data collected from large numbers of Muslim citizens in multiple predominantly Muslim states, as well as in Israel and the Palestinian territories, over multiple post-9/11 years in order to assess the current counterterrorism climate and anticipate its future. Original analysis of polling data from the Pew Research Center’s Global Attitudes Project was conducted for the 2011 calendar year. The analytic exercise illustrates how open source intelligence (OSINT) can be used to provide PSYINT for counterterrorism. The findings, many of which were counterintuitive, highlight the importance of testing theories and hypotheses about the bases of terrorism and political violence with statistical data on people’s attitudes, beliefs, sentiments, and other characteristics. The exercise also underscores how much work could be done with the available data. The present report merely illustrates some types of analyses that could be conducted in the service of improving defense and security through behavioral science.
Can Thematic Content Analysis Separate the Pyramid of Ideas from the Pyramid of Action? A Comparison Among Different Degrees of Commitment to Violence–Dr. Peter Suedfeld, Mr. Ryan W. Cross, and Mr. Carson Logan (The University of British Columbia): The publicly accessible messages of 15 extremist groups were coded by Thematic Content Analysis (TCA). Orientations toward violence included activist, militant, and terrorist groups; their goals derived from animal rights, Islamist, territorial, or white supremacist ideologies. TCA is a set of scientifically rigorous methods for converting running text into quantitative data, analyzable by standard statistics. A measure of cognitive integrative complexity (IC) showed significant declines across groups as they increased in their acceptance of violence, higher power imagery for terrorist compared to the other groups, and high importance among terrorists on the values of self-direction (autonomy), character (virtue, sincerity, honor), and benevolence (caring for those close to oneself). The results demonstrate the usefulness of IC coding to assess groups’ acceptance of, and proneness to, violence.
Prevention of Violent Extremism Based on Promoting Value Complexity, Informed by Neuroscience and Deployed on the Internet–Drs. Sara Savage and Jose Liht (University of Cambridge, UK): Researchers in counterterrorism are in a knowledge arms race that seeks to utilize the internet as a site for engaging with extremism and to harness neuroscience to inform counterterrorism strategies that can be deployed on-line. An approach to broad-based primary prevention that operationalizes Dr. Peter Suedfeld’s construct of integrative complexity (IC), developed by Savage & Liht at the University of Cambridge, leverages value complexity as a means to increase the complexity of thinking about issues of potential cleavage between Muslim and British/western identities. The IC model shows significant empirical results (using integrative complexity and values coding) across three different cultural groups exposed to AQ-related extremism, intra-religious and inter-religious conflicts, respectively. The IC approach is suitable for deploying on the Internet. Integrative complexity has two aspects: differentiation and integration. Differentiation regarding issues exploited by extremists will be supported through a range of balanced, even-handed film clips of influential Muslim viewpoints linked with vetted websites covering viewpoints such as: a) Caliphate, b) Conservative/Salafi, c) Muslim Engaged with the West, and d) Hardline/extremist views. This approach relativizes extremist opinion without provoking reactance. Graphic and video game learning activities will help users to ‘ladder down’ to the values that underlie the different viewpoints so that participants learn to find trade-offs between values in conflict and larger integrative frameworks, thus leveraging the complexity with which they think about issues that radicalisers exploit. This develops pro-social conflict skills and neutralizes the mobilizing impact of extremist opinion. The paper concludes with a research design to neuro-image the impact of the IC approach when operationalised on-line. This neuroscience research will augment the significant cognitive and social psychological data already supporting the IC approach. A project to develop an on-line version of the IC model Being Muslim Being British is planned in the UK.
Lone-actor Terrorists: Two Possible Profiles–Drs. Clark McCauley and Sophia Moskalenko (Bryn Mawr College): Research has shown that group-based terrorists vary in many ways; there is no useful profile of group-based terrorists. Lone-actor terrorists are relatively rare but may have personality and social characteristics that would support a useful profile. This paper will review recent research to suggest two possible profiles of lone-actor terrorists: the disconnected-disordered profile and the caring-compelled profile.
Psychological Risk Factors of Terrorism–Maj. Jason Spitaletta (Johns Hopkins University):
Counterterrorism is not necessarily about combating a phenomenon or its’ tactical manifestation, rather it is countering those who perpetrate the associated acts. There is no empirically based psychological or demographic profile of such a person that would indicate a predisposition toward joining violent extremist organizations. There are, however, environmental, social, and individual characteristics whose presence may increase the likelihood of participating in an act of terrorism. What follows are a proposed set of individual psychological risk factors for individual radicalization. The behaviors or attributes described merely point to a possible increase in the willingness to participate in or actual perpetration of political violence. While derived from the limited available empirical evidence, additional research is still required to validate these risk factors and ultimately establish them as indicators and warnings of terrorist behavior.
Leveraging Advances in Qualitative Methodology to Analyze Radicalization: Dr. Peter S. Henne, Mr. Jonathan Kennedy, Dr. John P. Sawyer, and Mr. Gary A. Ackerman (DHS/START Consortium/University of Maryland): The dearth of scholarly work on radicalization at the turn of the century has been replaced with a plethora of frameworks and theories to explain why and how individuals radicalize to extremist violence. This dizzying menu of explanations often makes it difficult for scholars and policymakers to assess how the many hypothesized causes across various levels of analysis interact with each other to produce a wide range of radicalization outcomes. Worse yet, the inferential power, and thus the policy applicability, of these studies are severely limited by the failure to identify and study the proper population of “negative cases.” Fortunately, there have been a number of qualitative methodological advances that can be used to bring greater structure to our understanding of radicalization. Specifically, this paper explores how the use of typological theories, two-level concepts, qualitative comparative analysis (QCA) and the possibility principle can serve as the starting point for integrating extant knowledge about radicalization and serve as a conceptual “first-step” to organize theories and evidence in preparation for a quantitative study.
Mechanics of the Toolbox: CVE Practice and Inform & Influence Activities–Mr. Mubin Shaikh (University of Liverpool, Tactical Decision-making Research Group): Public and practitioner discourse on countering violent extremism (CVE) speaks of “countering ideology” without providing the specific mechanics of how such a process would work. This article demonstrates how that is best achieved in a manner that respects the various mandates in which both the state and “other” cultural constructs interact with one another. As one definition of Inform and Influence Activities (IIA) has it, the Commander is to build teams—Joint and Interagency (and community) partners—to understand the information that comes from complex environments in order to influence the behavior of friends and adversaries.
Contributing Authors
Mr. Gary Ackerman (DHS/START Consortium, University of Maryland); Brig Gen David Béen (Deputy Director for Global Operations, J39); Maj David Blair (Harvard University); Mr. Ryan Cross (University of British Columbia); Dr. Bill Durodié (Royal Roads University); LTG Mike Flynn (Director, Defense Intelligence Agency); Dr. Peter Henne (DHS/START Consortium, University of Maryland); Mr. Jonathan Kennedy (DHS/START Consortium, University of Maryland); Mr. Scott Kesterson (Asymmetric Warfare Group); Dr. Jose Liht (University of Cambridge, UK); Mr. Carson Logan (University of British Columbia); Dr. David Mandel (DRDC Toronto); Dr. Clark McCauley (Bryn Mawr College); Dr. Sophia Moskalenko (Bryn Mawr College); Dr. Rodrigo Nieto-Gomez (Naval Postgraduate School); CAPT Wayne Porter (Naval Postgraduate School); Dr. Sara Savage (ICthinking® Research Group); Dr. John Sawyer (DHS/START Consortium, University of Maryland); Mr. Mubin Shaikh (University of Liverpool); Dr. Valerie Sitterle (Georgia Tech); Maj. Jason Spitaletta (Johns Hopkins University); Dr. Peter Suedfeld (University of British Columbia)
South Asia II: NSI Pathway Indicators–Pakistan’s Future: Analysis of the Fragmentation and Muddling Through Hypotheses.
Authors: Dr. Allison Astorino-Courtois, Dr. Belinda Bragg, Danielle Brickman, Sarah Canna, Abigail Desjardins, George Popp, Robert Popp, and Richard Williams (NSI, Inc).
This report supported SMA’s Geopolitical Stability in South Asia project. For additional information, please visit the South Asia project page.
This report explores the potential pathways associated with two hypothetical futures for the nation of Pakistan–Fragmentation and Muddling through. We started with theoretical propositions about the nature of, and points along, the pathways, tested these against historical cases, refined our characterizations of the paths, and then applied these to look at Pakistan from today forward.
NSI’s contribution to the futures portion of the South Asia SMA Follow-on effort explores the potential pathways associated with two hypothetical Pakistani futures–national Fragmentation and Muddling. We started with theoretical propositions about the nature of, and points along, the pathways, tested these against historical cases, refined our characterizations of the paths, and then applied these to look at Pakistan from today forward. At any point we might observe, in a state such as Pakistan, evidence consistent with any number of future pathways. For this reason, our approach was not to determine solely which path Pakistan is on, but where the balance of the evidence lies–which path may be dominant—and then search for indications and warnings (I&W) of what we should expect to see as further evidence of that path. The general paths provide a framework that easily could be applied to assess conditions in any state: for example, where Turkey is relative to a fragmentation outcome or whether Afghanistan is moving forward or slipping backward in political, economic, and social development.
NSI first defined and delineated the Fragmentation and Muddling pathways, and then identified a set of primary economic, social, and political markers drawing on empirical analysis and theoretical work. We then undertook a series of structured case studies to identify and distinguish between necessary and sufficient conditions for each pathway and to identify the most likely temporal orderings along each path. This research provided us with a descriptive analysis of each of the pathways: their necessary antecedent conditions, catalyzing events that propelled movement down a pathway, markers associated with that pathway, and any buffers or barriers that acted as roadblocks to further progression toward a fragmentation or muddling outcome.
This report first presents the findings of our analysis of Pakistan’s current position on the fragmentation and muddling pathways. This includes indicators and warnings (I&W) of further movement along each pathway, both those that signal increasing instability and those that suggest a strengthening of state social and political institutions and conditions. The second section of the report provides greater detail regarding the definition of each of the pathways and their associated markers. The third section presents an overview of the findings from our structured case study analyses that informed the development of the final marker lists for each pathway. Detailed case study summaries and analysis are provided in the appendix to this report.
Summary of Results
Since Pakistan’s loss of East Pakistan (current day Bangladesh) in 1971, a number of Pakistan scholars and observers have warned of further fragmentation of the state. Causes cited range from internal social cleavages to a nefarious U.S. government plot to weaken Pakistan (Choussedovsky, 2012). A second school of thought, however, proposes that Pakistan’s future will be characterized by “Muddling through”—that is, achieving neither positive political, economic, and social growth nor complete failure in these areas. This report identifies indications and warning measures associated with these two potential future pathways for the state of Pakistan.
At any point we might observe, in a state such as Pakistan, evidence consistent with multiple future pathways. For this reason, our approach was not to determine which single path Pakistan might be on but to
- use the data to suggest which might be the dominant path;
- use the general path models to highlight key political, economic, and social “pathway markers” as indicators of movement along one path; and
- provide suggestions of what conditions and events analysts should watch for in terms of further evidence of that path.
Below are summaries of the key findings of this study. The full pathway models and analyses of these in the case of Pakistan appear in the main body of this report.
Finding 1: Fragmentation
While most of the precipitating conditions are present, fragmentation of the Pakistani state is not imminent.
Nearly all of the antecedent conditions, necessary conditions, and important pathway markers for fragmentation are present in Pakistan today: state sovereignty contested violently by insurgent groups (e.g., in Balochistan, the FATA, and Kashmir); enduring disputes between geographically-associated social, ethnic, and economic groups; publically expressed conflict among elites in a country where political rivalries are numerous and intensely regional; and some public discontent over how the state is run. What explains Pakistan’s failure to fragment?
First, the absence of either a suitably catalyzing event or a willing external sponsor blocks the emergence of a single group with sufficient capacity to defeat the Pakistani state and break away successfully. Second, internal buffers— including institutional weaknesses at the provincial level that hinders attempts to devolve power and emerging signs of the Sharif government’s willingness to negotiate grievances with groups in FATA and Balochistan—serve as important buffers to fragmentation; however, most importantly, the external existential threat posed by India persists as a uniquely powerful and credible impetus for Pakistan’s disparate parts to remain united behind a common identity and narrative of victimization.
I&W for movement toward fragmentation
- A catalyzing event such as the 1970 cyclone in Bangladesh or publication of the Awami League’s Six-Point Program
- The appearance of a sponsor willing to provide the financial and/or security support to enable a group to break away from the central government (Pakistan’s status as a nuclear state may have raised the cost of this activity for neighboring states)
- The removal of buffers manifest for example in increased repression by the government; unwillingness to negotiate with disaffected groups; and normalized relations with India that weaken common narratives of Pakistani national identity and strengthen or incentivize regional identities
Finding 2: Muddling
Overall, the dominant trajectory of social and political development is slow decline (“Muddling Down”); although, there are signs that improvement is possible. Economically, the overall trajectory is flat (“Muddling through”) in large part due to the downward pull of political and social markers.
Political Markers: As of the date of this report (October 2013), data on political markers suggest that political development in Pakistan is on a downward path as nearly all of the key “Muddling Down” path markers—contested national sovereignty; weak and ineffective governing institutions; a weak and often biased justice system; uneven and insufficient internal revenue generation; contested civilian, military and judicial roles; limited provision of government services; and politics heavily influenced by corruption and patronage—are both present and substantial. Moreover, many of these path markers are quite well established at levels that presage continued deterioration. For example, Pakistan’s decades-long experience with weak governing institutions, biased justice, and uneven provision of services persistently weakens popular support for, and grants of, legitimacy to the government, which further weakens institutions and provision of services. In another example, fewer than one million Pakistanis (0.7% of the population) filed income taxes in 2001. At that time, the Taskforce on Tax Reform noted that “if taxes relative to GDP do not increase significantly, without new levies, Pakistan cannot be governed effectively, essential public services cannot be delivered, and high inflation cannot be avoided” (Taskforce on Reform of Tax Administration, 2001). However, tax revenues cannot be increased unless the tax base is increased or tax evasion is eliminated. More than ten years later, the government has failed to introduce general sales tax reform, raise energy prices, or reduce subsidies in the power sector, all of which would significantly increase government revenues (The World Bank, 2011).
I&W for further decline toward political instability
- Evidence that governing institutions are remaining weak and ineffective—such as increasing public criticism of and protest against the government and the call for better and/or more equitably distributed services such as energy and education—suggest that satisfaction with and loyalty to the government is receding leaves open space for radicalized political actors that would not necessarily seek liberalized and stable governance
- Strengthening of sub-national identities and/or alliances among insurgent, opposition, or grievance groups
I&W for reversal of the political “Muddling Down” trajectory
- Government efforts to apply rule of law fairly across all groups and significant reductions in human rights abuses by the state
- Consistent and adequate internal revenue generation and continued improvement in representation of minority views
- Resolution of internal sovereignty challenges
Economic Markers: Despite continued poor conditions and difficulties with economic planning and management, economically, Pakistan appears to be on the cusp between slow decline (“Muddling Down”) and a flat trajectory (“Muddling through”). Many of the markers common to economic “Muddling Down” pathways are present and significant in Pakistan. However, there are also important markers of slow but positive economic development (“Muddling Up”) to suggest an overall “Muddling through” trajectory. Even as several markers show continued deterioration over time or remain stagnant at detrimental levels, others show positive signs of improvement and buffers to complete economic failure appear to play a key role.
GDP growth appears to be on the decline, if somewhat unevenly. Real GDP growth has averaged only 3% over the last four years and has been on a volatile negative course since the early 1980s. Some growth spurts, like the one from 2004-2007, saw growth averages over 7%, but overall Pakistan’s economic growth has been insufficient, relative to its population growth (The IMF estimates that 7% GDP over an extended period is needed to absorb Pakistan’s nearly 2 million new labor market entrants each year IMF 2012). The result is high underemployment, unpaid employment, informal employment, and employment abroad: none of which maximize the productivity of Pakistan’s human capital.
Poor economic management, limited foreign investment, and a reliance on foreign aid/loans are also significant markers for Muddling Down in Pakistan.2 At the same time, Pakistan’s reliance on international aid has remained high and Pakistan ranks in the bottom third of 185 countries surveyed on ease of doing business there primarily due to its poor record on enforcing business regulations (World Bank, 2011). For example, Pakistan introduced a patent law in 2000, but does not have an effective system in place to prevent the issuance of marketing approvals for copies of patented pharmaceutical products. Pakistan authorities continue efforts to uphold intellectual property rights, but the country remains on the priority watch list of the U.S. Trade Representative (U.S. Office of the Trade Representative, 2013).
Despite the frequency of markers of a “Muddling Down” pathway, current economic conditions in Pakistan also include important markers of positive growth. For example, while insufficient energy resources hamper the economy, Pakistan boasts transportation infrastructure and irrigation systems adequate to support fundamental commerce in agriculture and manufacturing. The challenge is to maintain the infrastructure that exists and to expand these networks going forward. Pakistan also has relatively low unemployment rates, even if official numbers are artificially suppressed by sizable employment in the informal economy. Although Pakistan’s economy is not widely diverse, commodity prices for primary exports, like cotton, have grown. Continued improvements for these markers could help to reduce Pakistan’s reliance on foreign aid to balance its accounts. Finally, it is also encouraging to note that, even though inefficiencies of enforcement and management appear to be restricting the formal economy, Pakistan has sought to meet World Trade Organization expectations by creating appropriate regulations and policies that foster growth, making the prospects for future growth and
Muddling Up more favorable. To date, economic failure in Pakistan appears to have been buffered significantly by a thriving informal economy that provides access to jobs and alternative regulations or services that ensure supplemental productivity alongside the formal economy.
I&W for movement toward economic collapse
- Evidence showing that financial institutions continue to weaken
- Precipitous reduction or loss of alternative funding sources
- Continued government budget deficits
- Deterioration of transport, water, electricity infrastructure, and security, leading to capital flight and loss of foreign investment
I&W for movement toward economic development
- Diversification and growth in industrial production
- Reduced losses and business expenditures related to corruption
- Continued improvements in representation and governing legitimacy
Social Markers: The majority of the path markers for social disintegration are both present and significant in the case of Pakistan. Additionally, many of the markers show continued deterioration over time or remain stagnant at detrimental levels. However, unlike political and economic Muddling, Pakistan faces significant barriers to positive development (“Muddling Up”) in the social sphere. As of October 2013, only two of the path markers, but nearly all of the barriers commonly associated with positive societal development, are present in Pakistan.
Pakistan’s trajectory of socially “Muddling Down” is driven largely by its entrenched social divisions and high degree of cleavage between both religious and ethnic groups. For the most part, its provinces are distinct ethnic enclaves; its cities mirror the same divisions by neighborhood. Both Urdu and English are recognized as official languages, but Punjabi, Pashto, Sindhi, and Balochi are all dominant languages in their respective provinces. In addition to the distinct ethnic makeup of the provinces, Pakistan has three semi-autonomous regions: the Federally Administered Tribal Areas (FATA) and the disputed territories of Gilgit-Baltistan and Azad Jammu and Kashmir. The FATA has no representation in the National Assembly and Kashmir resembles an area under martial law, with strict Pakistani government oversight and heavy military presence.
In light of these circumstances, violent political action and terrorism are common, particularly in the FATA and Balochistan, where the Pakistani Taliban and related groups espousing Islamic extremism and Baloch nationalist insurgents respectively have openly engaged in conflict with the Pakistani Army for more than five years. In both cases, the government is perceived as illegitimate for its inability to provide equal access to goods and services or proportional representation in decision-making. For example, Balochis have a long-standing grievance that their province provides 36% of Pakistan’s natural gas supply, yet piped gas is only available to four of Balochistan’s 28 districts (International Crisis Group, 2006). As the violence that characterizes these frontier areas is also present as a microcosm in urban areas, with Karachi being the prime example, organized criminal outfits such as D-Company and the Lyari gangs have taken advantage and also contribute to high crime rates in the cities.
With Punjabis, Sindhis, and Muhajirs holding the majority of political power nationally and operating exclusive patronage networks, Pashtuns and Balochis, among others, have played the part of the marginalized in Pakistani society either through institutionalized discrimination (biased justice and under-representation) or through relative deprivation (fewer resources allocated for development). According to the United Nations Development Program’s Human Development Index (HDI), between 1980 and 2012 Pakistan’s HDI rose by 1.3% annually from 0.337 to 0.515 today, which gives the country a rank of 146 out of 187 countries with comparable data. The HDI of South Asia as a region increased from 0.357 in 1980 to 0.558 today, placing Pakistan below the regional average (UNDP, n.d.). Balochistan and the predominantly Pashtun province of Khyber Pakhtunkhwa (KPK) have the highest poverty rates based on the government’s most recent Socio-Economic Living Standard Measurement Survey (Pakistan Institute of Development Economics, 2011).
In addition to these social cleavages and socio-economic inequalities, markers for out-group focused religious extremism and violence are also present in Pakistan. Various degrees of Islamic extremism in particular can be found across the FATA, Balochistan, Kashmir, and other areas of the country, influenced by wealthy Arab donors to seminaries and mosques or local sectarian leaders. Though a majority of Pakistanis adheres to the teachings of Sunni Islam, some Shi’a Islam and Christian communities also exist. Violent clashes between extremists in these sects are not uncommon.
Despite entrenched cleavages and widespread insecurity, there are some markers for social Muddling Up. Most notably, upward social mobility is significant and present. Pakistan’s middle class has experienced steady growth, signaling an increase in opportunity for many. Further, though overall poverty levels remain high, Pakistan has the inherent capacity to meet the basic needs of its population with more effective and efficient application of effort. Pakistan’s largest cities are also examples of relatively positive ethnic integration and present notional models for achieving more tolerance in peripheral areas.
As with political Muddling and Fragmentation, the most significant buffer to social disintegration or continued Muddling Down in Pakistan appears to be the perceived presence of an external threat, which creates a common national identity to trump religious, ethnic, or regional ones. In Pakistan, the common perceived external threat is most often India (Balochistan and Kashmir), but in certain social contexts (the FATA) may also be the United States, due to frequent drone strikes. Should the willingness of the current Sharif government to negotiate with Baloch nationalists and Islamic insurgents in the FATA lead to real dialogue and institutional action that addresses the grievances of those who see themselves as marginalized, ethnic cleavages may soften and perceived inequality or relative deprivation may subside, as well as give extremists less credibility. Mitigating or removing these kinds of barriers could be the first step towards socially Muddling Up in Pakistan.
I&W for movement toward social collapse
- Further institutionalization of discrimination or marginalization of particular groups
- Continued rise in crime and violent dispute resolution
I&W for movement toward social development
- Expansion of social norm barring out-group focused violence
- Major social groups no longer perceive marginalization or discrimination and have equal access to public goods
- Safe and relatively secure environment, low crime
- Sustained economic growth

Looking Back, Looking Forward: Perspectives on Terrorism and Responses to It.
Author | Editor: Cabayan, H. (Joint Staff), Sitterle, V. & Yandura, M. (Georgia Tech).
This white paper is a follow-on report to a recent publication entitled “Over a Decade Later…What Now? What Next? A Multi-Layer Assessment of Terrorism in its Current and Future Manifestation.” 2 The previous paper was primarily an analytical product intended to provide insight into what current social science research and over a decade of practical experience suggest regarding the most effective counterterror strategies. It was based on comments made during multiple, semi-structured telephone interview sessions conducted between 06 May and 12 June 2013. The current white paper includes a series of articles by authors who participated in the previous white paper. These articles expand on the main themes raised in the previous report and cover topics ranging from strategic and adaptive considerations of terrorism to analytical considerations.
The various contributors to this volume advance insights that are summarized below:
- There is a body of research relating the strategic application of systems thinking, complexity theory, and complex adaptive systems theory to strategic planning in business and a variety of organizational constructs. These have implications in the deliberate planning of regional and global strategies and, critically, to our current counterterrorism strategy.
- We frequently seek clarity by way of attributing political or particular ideological reasons and affiliations behind terror acts when such attribution is really viewing the present and future through the lens of the past. Looking forward, real resilience requires having a narrative of our own that projects a purpose beyond responding to adversity. Furthermore, we will continue to be perplexed by the enemy in our counterterrorism strategy as long as we are unclear as to our own purpose and direction.
- The convergence of rapidly advancing scientific sectors (biotech, nanotech, energy, materials, etc.) combined with the availability of CBCT (Cyber-Based Communication Technology) could produce an entirely new generation of threat capabilities. The evolving socio-technical ecosystem is transforming temporal and spatial characteristics from individual to trans-State behaviors, simultaneously creating new paradigms for emergence and support of terror activities on a global scale.
- As terrorism adapts to the market place, we need to move from “terrorist” towards an understanding of market entry and risk mitigation. The “cost” of terror and of counterterror activities is an increasingly important perspective. Turning the lens on ourselves, we need to ask what it will take to compete, to grow, and to expand our own market share, and re-establish our national identity as a global consumer brand of choice.
- There is a need for much better psychosocial intelligence on foreign public opinion regarding key issues. Open-source intelligence can be used to provide such intelligence for counterterrorism. Findings from on-going efforts highlight the importance of testing theories and hypotheses about the bases of terrorism and political violence with statistical data on people’s attitudes, beliefs, sentiments, and other characteristics.
- Thematic Content Analysis (TCA) of activist, militant, and terrorist groups has demonstrated the usefulness of such analyses to assess groups’ acceptance of, and proneness to, violence. An approach based on this concept and using measures of integrative cognitive complexity has been operationalized and proven successful for primary prevention. Efforts are underway for deploying this capability on the Internet.
- Lone-actor terrorists have been relatively rare thus far. They may, however, exhibit personality and social traits that would support a useful profile, unlike group-based terrorists who vary in a myriad of ways. Recent research suggests two possible profiles of lone-actor terrorists: the disconnected-disordered and caring-compelled profiles.
- Similarly, there is presently no empirically based psychological or demographic profile of individuals that perpetrate terrorist acts indicating a predisposition toward joining violent extremist organizations. Based on what limited empirical evidence is available, however, a set of individual psychological risk factors for individual radicalization may be proposed. While more study is needed before these may be established as firm indicators, these individual-level attributes may provide a starting point toward profiling individual willingness to participate in or perpetrate political violence.
- There are a myriad of theories and frameworks to explain why and how individuals may radicalize to violence, and many shortcomings remain that limit the validity and generalizability of the findings. Advances in qualitative methodologies offer a framework for improving the understanding of the complexity inherent in the phenomena of radicalization and non- radicalization. Improved understanding of the multiple potential pathways into radicalism and terrorism should lead to better-tailored CVE (countering violent extremism) policies that are more effective and efficient.
- There is a need to build teams—Joint and Interagency (and community) partners—to understand the information that comes from complex environments in order to organize counterterror practices in ways that inform and influence the behavior of friends and adversaries.
Brief Topic Overviews
Rethinking Counterterrorism: The Need for Systemic Strategic Planning and a Strategic Campaign to Address Violent Islamist Extremism that Manifests Itself in Terrorist Acts–CAPT Wayne Porter (NPS): There is a body of research related to strategic planning in an uncertain and dynamic environment. This research includes, among other topics, analyses of the strategic planning and thinking process, organizations and strategic change, multi-national corporation strategic planning in times of turbulence and uncertainty, backcasting for strategic planning of sustainable development, cognitive biases on strategic planning, and sensemaking in the boundaries of stability and instability, order and chaos. Further research is needed, though, in analyzing the potential benefit of employing methods of system thinking and complexity in the deliberate planning of regional and global strategies. Critically, this applies to our current counterterrorism strategy and the phenomenon of ideologically based violent extremism. While this paper focuses primarily on radical Islamist extremism, the concepts discussed apply equally to any ideologically based extremist network seeking to employ terrorism.
War on Terror or a Search for Meaning?—Dr. Bill Durodié, Professor & Program Head, Conflict Analysis & Management Programs, School of Humanitarian Studies, Royal Roads University: The events of 9/11 necessitated a response. What shape that took was determined by the meaning attributed to those events, in its turn influenced by the mood of the times. Unfortunately, these latter elements reflected the sense of confusion that gripped the West in the aftermath of the Cold War. This paper argues that we will continue to be perplexed by the enemy in the war on terror so long as we are unclear as to our own purpose and direction. Indeed, the perpetrators of such acts today appear more influenced by Western dystopianism than Eastern mysticism. Real resilience requires having a narrative of our own that projects a purpose beyond responding to adversity.
Technology, Society, and the Adaptive Nature of Terrorism: Implications for Counterterror–Dr. Valerie Sitterle (Georgia Tech), Dr. Rodrigo Nieto-Gomez (NPS), Maj David Blair (Harvard University): As technology continues to advance and increasingly permeate society, generating violence that makes a societal group feel vulnerable is not difficult. Generating the desired interpretation of that violence is hard, however, and is critical to the coupling we need between future U.S. counterterrorism (CT) and information operations (IO) strategy. This latter space, with all of its socio-technical nuances, is where threats we classify as “terrorists” have excelled. This paper will begin by explaining the nature and importance of socio-technical complexity and its relevance to terroristic adaptation. A true socio- technical confluence perspective, distinct from the traditional view that treats the dimensions as distinct elements that happen to coexist, promotes awareness of active and passive influences that exist bi- directionally between the social and technological elements. The cyber realm then becomes both a means through which terroristic attacks are conducted or directly targeted and an ecosystem. In this latter view, individual and community (up to state and even trans-state) patterns of organization are transformed via completely new paradigms across temporal and spatial scales of communication and information sharing across societal sectors. This has significant ramifications for emergence of terror cells, their coordination, and passive support of their activities in a global scale. Behavior of terror cells in this complex environment may be more intuitively understood from an entrepreneurial business model analogy, which naturally expands into a consideration of the multiple dimensions associated with both conducting terror and striving to build protective measures against it. Since adaptation is a hallmark of living systems, the U.S. cannot stifle innovative advances by a terroristic adversary through reliance on a static U.S. counterterror strategy. Rather, the U.S. must lead disruptive innovation in order to drive strategic surprise and strain the capacity of these threat groups to adapt.
Market Economies and the Collision of Narratives…Approaching Terrorism Through Branding and Marketing Methodologies–Mr. Scott Kesterson, Asymmetric Warfare Group: Terrorism has become a global franchised business, and, in terms of brands, al-Qa’ida (AQ) is king. Their brand has come to guarantee global positioning, brand name recognition, easy recruiting, as well as abundant financial resourcing. With the loss of Osama bin Laden, however, al-Qa’ida’s brand supremacy is now vulnerable to new tiers of competition; their brand that could have been characterized by adaptability, innovation, and persistence has suffered a loss of consumer confidence. As terrorism adapts to the market place, our conversations need to move from “terrorist” towards an understanding of market entry, branding, and risk mitigation. What are the market factors that create brand durability for terrorism? What are the value propositions that these markets are responding to? What are the market elements that allow for growth and the ability to franchise? Turning the lens on ourselves, we then need to ask what it will take to compete, to grow, and to expand our own market share and re-establish our national identity as a global consumer brand of choice.
Counterterrorism and Muslim Public Opinion–Dr. David R. Mandel (DRDC Toronto): A widely shared view is that counterterrorism must address the psychosocial and cultural aspects of Islamic violent extremism if it is to succeed strategically. Another is that we need much better psychosocial intelligence (what might be called PSYINT) on Muslim public opinion regarding key issues. In this paper, the author draws on open source polling data collected from large numbers of Muslim citizens in multiple predominantly Muslim states, as well as in Israel and the Palestinian territories, over multiple post-9/11 years in order to assess the current counterterrorism climate and anticipate its future. Original analysis of polling data from the Pew Research Center’s Global Attitudes Project was conducted for the 2011 calendar year. The analytic exercise illustrates how open source intelligence (OSINT) can be used to provide PSYINT for counterterrorism. The findings, many of which were counterintuitive, highlight the importance of testing theories and hypotheses about the bases of terrorism and political violence with statistical data on people’s attitudes, beliefs, sentiments, and other characteristics. The exercise also underscores how much work could be done with the available data. The present report merely illustrates some types of analyses that could be conducted in the service of improving defense and security through behavioral science.
Can Thematic Content Analysis Separate the Pyramid of Ideas from the Pyramid of Action? A Comparison Among Different Degrees of Commitment to Violence–Dr. Peter Suedfeld, Mr. Ryan W. Cross, and Mr. Carson Logan (The University of British Columbia): The publicly accessible messages of 15 extremist groups were coded by Thematic Content Analysis (TCA). Orientations toward violence included activist, militant, and terrorist groups; their goals derived from animal rights, Islamist, territorial, or white supremacist ideologies. TCA is a set of scientifically rigorous methods for converting running text into quantitative data, analyzable by standard statistics. A measure of cognitive integrative complexity (IC) showed significant declines across groups as they increased in their acceptance of violence, higher power imagery for terrorist compared to the other groups, and high importance among terrorists on the values of self-direction (autonomy), character (virtue, sincerity, honor), and benevolence (caring for those close to oneself). The results demonstrate the usefulness of IC coding to assess groups’ acceptance of, and proneness to, violence.
Prevention of Violent Extremism Based on Promoting Value Complexity, Informed by Neuroscience and Deployed on the Internet–Drs. Sara Savage and Jose Liht (University of Cambridge, UK): Researchers in counterterrorism are in a knowledge arms race that seeks to utilize the internet as a site for engaging with extremism and to harness neuroscience to inform counterterrorism strategies that can be deployed on-line. An approach to broad-based primary prevention that operationalizes Dr. Peter Suedfeld’s construct of integrative complexity (IC), developed by Savage & Liht at the University of Cambridge, leverages value complexity as a means to increase the complexity of thinking about issues of potential cleavage between Muslim and British/western identities. The IC model shows significant empirical results (using integrative complexity and values coding) across three different cultural groups exposed to AQ-related extremism, intra-religious and inter-religious conflicts, respectively. The IC approach is suitable for deploying on the Internet. Integrative complexity has two aspects: differentiation and integration. Differentiation regarding issues exploited by extremists will be supported through a range of balanced, even-handed film clips of influential Muslim viewpoints linked with vetted websites covering viewpoints such as: a) Caliphate, b) Conservative/Salafi, c) Muslim Engaged with the West, and d) Hardline/extremist views. This approach relativizes extremist opinion without provoking reactance. Graphic and video game learning activities will help users to ‘ladder down’ to the values that underlie the different viewpoints so that participants learn to find trade-offs between values in conflict and larger integrative frameworks, thus leveraging the complexity with which they think about issues that radicalisers exploit. This develops pro-social conflict skills and neutralizes the mobilizing impact of extremist opinion. The paper concludes with a research design to neuro-image the impact of the IC approach when operationalised on-line. This neuroscience research will augment the significant cognitive and social psychological data already supporting the IC approach. A project to develop an on-line version of the IC model Being Muslim Being British is planned in the UK.
Lone-actor Terrorists: Two Possible Profiles–Drs. Clark McCauley and Sophia Moskalenko (Bryn Mawr College): Research has shown that group-based terrorists vary in many ways; there is no useful profile of group-based terrorists. Lone-actor terrorists are relatively rare but may have personality and social characteristics that would support a useful profile. This paper will review recent research to suggest two possible profiles of lone-actor terrorists: the disconnected-disordered profile and the caring-compelled profile.
Psychological Risk Factors of Terrorism–Maj. Jason Spitaletta (Johns Hopkins University): Counterterrorism is not necessarily about combating a phenomenon or its’ tactical manifestation, rather it is countering those who perpetrate the associated acts. There is no empirically based psychological or demographic profile of such a person that would indicate a predisposition toward joining violent extremist organizations. There are, however, environmental, social, and individual characteristics whose presence may increase the likelihood of participating in an act of terrorism. What follows are a proposed set of individual psychological risk factors for individual radicalization. The behaviors or attributes described merely point to a possible increase in the willingness to participate in or actual perpetration of political violence. While derived from the limited available empirical evidence, additional research is still required to validate these risk factors and ultimately establish them as indicators and warnings of terrorist behavior.
Leveraging Advances in Qualitative Methodology to Analyze Radicalization: Dr. Peter S. Henne, Mr. Jonathan Kennedy, Dr. John P. Sawyer, and Mr. Gary A. Ackerman (DHS/START Consortium/University of Maryland): The dearth of scholarly work on radicalization at the turn of the century has been replaced with a plethora of frameworks and theories to explain why and how individuals radicalize to extremist violence. This dizzying menu of explanations often makes it difficult for scholars and policymakers to assess how the many hypothesized causes across various levels of analysis interact with each other to produce a wide range of radicalization outcomes. Worse yet, the inferential power, and thus the policy applicability, of these studies are severely limited by the failure to identify and study the proper population of “negative cases.” Fortunately, there have been a number of qualitative methodological advances that can be used to bring greater structure to our understanding of radicalization. Specifically, this paper explores how the use of typological theories, two-level concepts, qualitative comparative analysis (QCA) and the possibility principle can serve as the starting point for integrating extant knowledge about radicalization and serve as a conceptual “first-step” to organize theories and evidence in preparation for a quantitative study.
Mechanics of the Toolbox: CVE Practice and Inform & Influence Activities–Mr. Mubin Shaikh (University of Liverpool, Tactical Decision-making Research Group): Public and practitioner discourse on countering violent extremism (CVE) speaks of “countering ideology” without providing the specific mechanics of how such a process would work. This article demonstrates how that is best achieved in a manner that respects the various mandates in which both the state and “other” cultural constructs interact with one another. As one definition of Inform and Influence Activities (IIA) has it, the Commander is to build teams—Joint and Interagency (and community) partners—to understand the information that comes from complex environments in order to influence the behavior of friends and adversaries.
Contributing Authors
Mr. Gary Ackerman (DHS/START Consortium, University of Maryland); Brig Gen David Béen (Deputy Director for Global Operations, J39); Maj David Blair (Harvard University); Mr. Ryan Cross (University of British Columbia); Dr. Bill Durodié (Royal Roads University); LTG Mike Flynn (Director, Defense Intelligence Agency); Dr. Peter Henne (DHS/START Consortium, University of Maryland); Mr. Jonathan Kennedy (DHS/START Consortium, University of Maryland); Mr. Scott Kesterson (Asymmetric Warfare Group); Dr. Jose Liht (University of Cambridge, UK); Mr. Carson Logan (University of British Columbia); Dr. David Mandel (DRDC Toronto); Dr. Clark McCauley (Bryn Mawr College); Dr. Sophia Moskalenko (Bryn Mawr College); Dr. Rodrigo Nieto-Gomez (Naval Postgraduate School); CAPT Wayne Porter (Naval Postgraduate School); Dr. Sara Savage (ICthinking® Research Group); Dr. John Sawyer (DHS/START Consortium, University of Maryland); Mr. Mubin Shaikh (University of Liverpool); Dr. Valerie Sitterle (Georgia Tech); Maj. Jason Spitaletta (Johns Hopkins University); Dr. Peter Suedfeld (University of British Columbia)

