SMA Publications
NSI maintains an extensive Publications archive of government-sponsored research and analysis products, various research efforts from our professional and technical staff, and a variety of corporate news items. The government-sponsored products are maintained on behalf of the US Department of Defense (DOD) Strategic Multilayer Assessment (SMA) program and address challenging national security problems and operational imperatives.
The Human Domain: The Unconventional Collection and Analysis Challenge Workshop.
Author | Editor: Canna, S. & Popp, R. (NSI, Inc).
One of the major challenges the US has faced during the opening decades of the 21st Century is the growth in the number and international reach of insurgents, terrorists, WMD proliferators and other sorts of nefarious groups. Among many others, the current situation in Iraq illustrates the difficulty of countering insurgencies once they have become violent and operationally well-established. The apparent transition of contemporary war away from the traditional physical battlefield towards the human element as the battlefield poses new challenges for both intelligence and operations – collections and analysis within the human domain requires new thinking and new methods.
The purpose of this workshop was to identify approaches to recognize and anticipate the conditions in which insurgents, terrorists, WMD proliferators and other sorts of nefarious groups tend to emerge, become operationally established, and choose to employ tactics counter to the interests of the US national security objectives. An underlying presumption of this workshop is that tackling these movements during their emergent phases is less costly in resources and lives, with more non-lethal options available for consideration, than after they have become fully established. Novel approaches to collections and analysis of the interactions within and between elements of the “human dimension” may lead us to greater potential for proactive rather than reactive capabilities, and certainly non-kinetic capabilities, not only within the military context, but within all components of national power.
Clearly, focusing on emergent violent groups and their activities will necessitate a shift in how the nation and its allies collects, analyzes, and acts upon information from and about these volatile environments. The workshop brought together a diverse group of physical and social scientists, academics, analysts, intelligence collection managers, operational planners, and decision makers to discuss novel techniques and methods for a more proactive approach to address the human dimension associated with insurgents, terrorists, WMD proliferators and other sorts of nefarious groups, and the impact of such an approach on training, planning, tasking, collection, analysis, and decision making in the coming decades.
EVOLUTION OF VIOLENT EXTREMISM
There is an important distinction between activism and radicalism. Activism is legal and nonviolent political action, while radicalism is illegal and violent political action. Activism is not necessarily a conveyor belt to radicalism. Individuals can be radicalized from any layer of society including neutral parties, sympathizers, and activists.
Government Sponsored Research on Violent Extremism
The Department of Homeland Security (DHS) is is laying the groundwork to conduct in-depth case studies of individuals engaged in terrorist violence in the US. At the group level, DHS is studying terrorist group rhetoric with a focus on both groups that have engaged in terrorism and groups that would be considered radical but that have not engaged in terrorism. The study will look at groups with similar ideologies and goals and try to understand why some groups choose violence and others do not. DHS will also work to identify characteristics of groups who participate in IED attacks. At the community level, DHS is involved in two primary activities. The first is evaluating whether survey data can shed light on radical activity in the US. Finally, DHS is working with START to study the effectiveness of counter radicalization programs conducted in five countries including Yemen, Indonesia, Columbia, Northern Ireland, and Saudi Arabia.
The Behavioral Analysis Unit is the newest organization within the Federal Bureau of Investigation. It is an operational unit that conducts research. Counterterrorism research within the unit is still in its infancy stages; however, some projects are currently underway dealing primarily with operational threat assessments. The most pertinent research efforts are in collaboration with DoD intelligence units. This work primarily focuses on radicalization by looking at the radicalization process in historic case studies. The FBI is also involved in another research effort in coordination with the WMD directorate, to look at 50 domestic cases in which offenders used WMD in the US.
The Defense Intelligence Socio-Cultural Dynamics Working Group (SCDWG) was created in 2002 to develop an enterprise solution to institutionalize Socio-Cultural Dynamics intelligence analysis. The group was asked to address the full scope of issues, from policy to tactical. The group was asked to define the role of intelligence in this area as well as to identify the “right tool for the right job.”
The Marine Corps Intelligence Activity (MCIA) is working on the next generation of cultural intelligence. They are working on visualizing cultural intelligence by “putting culture on the map.” Their second project is to support influence operations and irregular warfare by building partner capacities focused on the values and themes of sub-national groups. The third is cultural vignettes, which are short and focused products designed to create a specific cognitive map for each mission set. The fourth is building an analytic capacity by supporting uniquely trained cultural analysts, ensuring 24/7 reachback for deployed unites, and creating deployable analytic teams for contingency operations.
UNDERSTANDING SOCIO-CULTURAL DYNAMICS: TRADECRAFT AND OBSERVATIONS FROM A DISTANCE
Studies to understand a country and its people must be planned and carried out with nuance. Ethnic maps, a critical tool for US forces, have long been a political issue. It affects resource allocation, boundaries, and political formulae. In countries experiencing ethnic conflict, building a credible demographic baseline must be done before lasting geopolitical stability can be realized. Maps can help researchers and analysts understand the cultural geography of conflict. Chorological analysis, relating to the description or mapping of a region, can reveal causal linkages and patterns of political and social behavior that researchers were previously unaware of. Mapping the human terrain is needed to understand these complex problems.
Culture at a distance methodology from 1942 mostly comprised of several sources. Researchers studied travelers’ accounts, ethnographies, histories and other second hand sources including social science works. Content analysis finds its roots in these attempts. Post World War II, the DoD funded a great deal of social science research although only a small part of it was “culture at a distance”. They focused instead on models such as game theory. Their main interest was in political instability: its causes and indicators.
Today, the DoD has stated that socio-cultural data collection is everyone’s problem. However, the DoD does not currently have the knowledge and understanding of non-Western cultures and societies necessary to execute these missions. Because of this, there are several new culture at a distance methods. Computational modeling has become the sine qua non of culture at a distance method, but it suffers from considerable handicaps. Its emphasis on computational engineering leads to “everything looks like a nail” thinking. The problem with models is that many do not scale gracefully from explaining small scale issues to larger scale ones. Models are culturally and socially ignorant, which is frequently the case when engineers develop “new cultural theory” with little or no training in the fields of social science.
Socio-Cultural Tradecraft and Open Source Collection Requirements Management
Emerging violent non-state actors use or share a common story about their involvement to motivate and empower their groups, and attract and mobilize their audiences. The degree by which infringements are interpreted, personified, and perceived is the variable to which violence emerges. It is typically a conflict between the haves and the have not’s over a particular issue. Modeling these relationships requires a four prong approach: anthropological research; open source collection; human intelligence collection; and environmental research. The model will synthesize that information to assess behavior.
Cultural geography is the study of spatial variations among cultural groups and the spatial functioning of society. Urban geography is the study of how cities function, their internal systems and structure, and the external influences on them and the study of the variation among cities and their internal and external relationships. The human geography areas of interest include economics, demographics, politics, culture, combined social implications, and technology/infrastructure. Cultural geographers face several challenges. First, experiences in Afghanistan and Iraq have shown that neighborhood level data is necessary for operational and tactical planning (Intelligence Preparation of Battlefield). Second, there is a lack of reliable data sets. For example, there has been no census in Lebanon since 1932. Third, closed countries, such as North Korea, pose a problem. Fourth, no city level data exists or it is difficult to obtain in grey literature. Fifth, there is a lack of current academic studies. Therefore, researchers must take a multidiscipline approach and use sources from a variety of fields to complete their research.
Remote Observing Using Large Data Sets
The nexus for computer forensics is addressing large data sets. Researchers and developers are working with open source information and applying analytic tools to it. They have discovered that it is considered novel in the US to use the same tool to address open source and classified datasets and merge them. One large data set, INSPIRE, was developed to allow an analyst to look at a large number of text documents and look for words and phrases. The program graphically portrays the output. A subsequent project is porting INSPIRE over to high power computing environment.</p>, <p>Content analyzers are another tool for working with very large datasets. The tool makes coding schemes in the process of creating large data sets from large text sources. It has an automatic generation process that is transparent. From this data, the analyst produces dashboard like metrics to describe the data. This has created an impetus to create measures of effectiveness and validation. The team discovered that people and computer coders make different types of errors. Humans make boredom errors. Their accuracy always goes down over time. However, if a computer sees a new word, it will not code it. The operation code measures how you present self and others in text on cooperative or conflictive dimensions. The tool can also extract and compare entities for distrustfulness. They use a combination of tools to look for themes and people. It is a pragmatic way to build structure while reducing the analysts’ reading load.
UNDERSTANDING THE HUMAN TERRAIN: TRADECRAFT AND STREETCRAFT METHODS
Applying Law Enforcement Methods to Gathering Human Terrain
An appropriate balance of skills, knowledge, and abilities need to be incorporated into an analysis team. It needs to be half Army Ranger company and half artist colony. Good analysts are adaptable, intellectually flexible, and have a high degree of comfort with ambiguity. An analyst’s job is simple: they read, write, and present. In the development of a good analyst, no preparation matches analyst’s comfort level with ambiguity. Furthermore, the depth and breadth of an analyst’s rolodex is more important than personal understanding of a region or topic. Analysts must also exhibit finesse - the practice of combining knowledge, thought, and intellectual stamina. Personal conviction of paying attention to a few small details that have enormous impact on outcomes or intelligence is critical. Good analysts are those who care as much about operational environment as producing a final product.
Approximately 90 percent of the food we eat, clothes we wear, and products we use are imported daily via commercial maritime transport. Threats to ships and ports include drug smuggling, stowaways, and terrorists. Drugs are often creatively hidden in cargo, such as cocaine stashed inside individual bananas. Drug couriers can also be hidden away in cargo shipments. These could easily be terrorists or terrorist materials. According to a US Coast Guard report, 25 Islamic extremists entered the US onboard commercial cargo vessels. Narco traffickers are more frequently taking consignments of extremists to the US. There is an increasing level of cooperation between MS-13, narco traffickers, and Islamists. The human collection component is critical to stopping these illegal activities because Customs cannot provide the level of analysis needed.
The Department of Commerce’s task is to prevent the export of US dual-use goods and technology that may be used by rogue states or terrorists to make chemical, biological or nuclear weapons. The Office of Export Enforcement’s priorities are WMD proliferation, terrorism/terrorist support, and unauthorized military/government use. Commerce is unique in that it has civil penalties, in addition to criminal penalties, in which one only needs the preponderance of the evidence to convict. The challenge of identifying and stopping illegal dual use exports is making sure at every step of the process that all of the people involved can validate the end use. It gets murky because end users lie and some components are working with the end users. Globalization is also a national security challenge and many transactions are moving over the internet. The US government does not move at the speed of business.
The Criminal Investigation Task Force (CITF) was created in early 2002 by the DoD to conduct investigations of detainees captured in the Global War on Terrorism. CIFT became the investigative arm of the DoD after OSD was given the mission to prosecute the detainees. OSD transferred the responsibility to the Army, where the CITF now falls under Army Criminal Investigation Command (CID). The need for analysts and intelligence professionals was huge, especially for law enforcement officials not used to working with classified materials. Likewise, law enforcement people need to communicate with the combatant commanders. Terrorists groups often act like organized crime groups. The intelligence community may not have much experience in this, but law enforcement does. It also has experience in conducting interrogations. To conduct interviews effectively the interrogator must put all biases aside and just accept the culture for what it is. The interrogator must get down to the bedrock of cultural foundation.
Applying Social Science Methods to Understanding the Human Terrain
Social science is the application of consistent, rigorous methods of research and analysis to describe or explain social life. Its purpose is inference: using facts we do know (data, observations) to learn about facts we do not know (theories, hypotheses). It is used to make descriptive inferences (semantic program); to place or make observations within a conceptual framework to allow people to understand a phenomenon; and to make causal inferences (syntactic / pragmatic program). Because of the large number of potential causal factors for any social phenomenon, establishing causation is difficult. If we can establish the cause of a social phenomenon, then we can make policy to affect that phenomenon.
Data collection involves various methodologies such as ethnography: participant observation; surveys: interview processes (formal, informal, group, individual, structured, unstructured); record or document review; and history: conducting interviews or reviewing documents about the past. Data analysis involves direct interpretation: analysis by an individual’s reflection and synthesis; quantitative analysis: using standard methods of statistics to ascertain relationships; and formal modeling: analysis by creating a formal system that mimics the world. In evaluating which method is most appropriate, it is important to keep in mind that multidisciplinary methods reinforce one another.
Field research in Iraq is particularly complicated. Researchers must use semantic programs and descriptive inference as well as create a pragmatic program with causal inference. Some of the challenges include sampling, reactive bias, and interpretive bias. Coping with these problems is done by working through local researchers, geographic sampling and purposive sampling, redundancy of methods, and redundancy of research networks. On the ground analysis is informed by area studies, topic specialization, and occasional forays into population.
There is a great need to improve intelligence support to stability operations. To do this, analysts must embrace the importance of understanding the human terrain. There are three key elements to the human terrain. The first is developing a socio-cultural dynamics data network and repository. The second is developing data gathering, visualization, and analytic tools. The third is recruiting, training, and deploying experts to support decision-making.
To understand counterinsurgency, you must first understand and define the elements involved. Collecting information for COIN operations involves identifying key groups in a society and representing where they are located on a map. For each group, researchers seek to identify security (level, sources, threats); income and services (level, sources, gaps); beliefs and communications systems (narratives, symbols, norms and sanctions); and authority structures & figures (identity, structures, levels of authority).
Soldiers as Human Terrain Sensors
The Civil Affairs (CA) information objectives were to provide multi-dimensional situational understanding, provide situational analysis, and to work on the development of possible solution sets. The foci of CA operations are human terrain identification and prioritization (sphere of influence management) and civil reconnaissance. Within the human terrain network, there are sphere of influence engagements. These works identified political/tribal leaders throughout the district and their areas of influence to facilitate reconciliation efforts. They also identified facility managers/public works workers to facilitate transition to Iraqis fixing Iraqi problems. They also prioritized efforts to optimize limited resources for engagement.
There are three critical nodes in the CA analysis process. The first is collection. The information is the critical base element to the process. Without this, there is no system. The second is consolidation. Analysis and understanding the information makes the process function. It is an art and a science. The third is dissemination. Sharing the situational understanding is the key to success. Dissemination must flow up and down in order to coordinate and integrate with partners.
Provincial Reconstruction Teams (PRTs) have become a key tool for the international community to assist Afghanistan in becoming a secure and self-sustaining Republic. They represent, at the local level, the combined will of the international community to help the government and the civil society of Afghanistan become more stable and prosperous. PRTs, due to their provincial focus and civil-military resources, have wide latitude to accomplish their mission of extending the authority of the Government by improving security, supporting good governance and enabling economic development. This engagement of diplomatic, military and economic power by Nations at the provincial level allied with the wide latitude to accomplish their mission has been a strength, as it provides flexibility of approach and resources to support the provincial government structures and improve security.</p>, <p>The Humanitarian Information Unit (HIU) serves as a United States Government (USG) interagency center to identify, collect, analyze and disseminate unclassified information critical to USG decision makers and partners in preparation for and response to humanitarian emergencies worldwide, and to promote best practices for humanitarian information management.
Civilians as Human Terrain Sensors
In order to operate effectively in Afghanistan, warfighters need to understand the cultural context and history of the nation. An anthropology background by itself is not always useful. Human Terrain Teams (HTTs) and others need culture specific knowledge to achieve their mission in foreign countries. An open source portal exists to provide a civilian based source of socio-cultural information on Afghanistan. The portal facilitates a subject matter expert network to encourage interaction among the key players including the Department of State (DoS), non-governmental organizations (NGOs), the US Agency for International Development (USAID), Brigade Combat Teams (BCTs), and soldiers. The site drills down to the provincial level where 21 of 34 provinces have been completed. The site provides information on detailed maps, refugees, education, health, topographic information, etc.
SUPPORTING ANALYTIC DISCIPLINES
Modeling and Visualization Workshop Summary
The objective of the Social Science Modeling and Visualization Workshop, held in January 2008, was to provide a “mixing bowl” for social scientists, modelers, researchers and government stakeholders to discuss the state-of-the-art in methods/models/visualization and their potential application in SMA efforts. Models can clarify complex situations, test assumptions, aid decision making, explore co-evolutionary motivations and bound the expected and outlier behaviors. Modeling can capture dynamical, non-linear processes. They can be multi-level, multi-scale behavior representations. Other benefits include that models can assist in training decision makers on the consequences of their policies/decisions. Visualization is a critical component of modeling. Therefore, it needs to be considered from the beginning of a project. Visualization serves a variety of functions include support of knowledge management, contextual visualization, relational visualization, identification of key features/nodes/information, understanding of decisions/complex processes, and evaluation/inspection of the data. Models must be verified, valid, and credible. The theoretic framework of social science modeling and visualization still needs work. Opportunities and challenges include the need for better, scientifically grounded theories. The federal government is interested in social science, but struggling to determine how to support it. It will take 4-5 years to reach robust funding levels.
Evolutionary Agent-based Modeling and Game Theoretic Simulations
Agent Based Modeling (ABM) is successful in the social science arena because as in the traditional approach to formal modeling, the goal is reducing the social landscape to a set of meaningful variables and specific mathematical equations. ABM brings to social science the ability to begin with a social landscape of entities in the world. It can identify basic relationships between actors. All models are developed or designed to answer a class of questions. ABMs are typically designed to answer questions that are intractable through earlier and more traditional mathematical or statistical methods, such as complex emergent patterns in large systems of agents. The beauty of ABM is that it can conduct experiments about shifting policies. All this can be done in silicon because you cannot manipulate players in the real world. ABM is a specific kind of simulation. It provides an experimental setting for finding patterns that are not very obvious.
Game theory is a branch of applied mathematics that formally models strategic behavior. Game theory is an approach to aid in articulating and understanding important factors of conflicts / disputes / coalitions. Game theory is neither prescriptive nor descriptive; nor is it normative. It is a theoretical tool. Game theory does not provide an answer; it provides a helpful way to frame the question to better understand the situation. If the assumptions are correct, game theory will provide an answer. Some assumptions of the theory include (bounded) rationality, complete information, and preference hierarchy for players (utility). In conclusion, it is important to remember that people are not agents. Game theory requires assumptions about behavior. It provides insight and understanding, but people are more complex than mathematical models. Finally, as in any model, if you put garbage in, you get garbage out.
Data Fusion / Integration and Detecting Patterns in Heterogeneous Data Sets
The defense and intelligence communities are making great progress in the social sciences. Many agencies now realize the importance of social science approaches, in combination with more traditional approaches. Often, people want to know why if we can go to the moon we cannot accurately model social science. It is because people are complex intelligent agents with feedback. They have multiple incentives, multiple allegiances, and multiple groups. Humans also exhibit adversarial behavior. They provide inaccurate and misleading information. Behavior is not invariant. There is a hierarchy of challenges in data fusion. The first is registration and entity resolution. The second is group and network detection. The third is feature construction and recognition. The fourth is complex event detection. The fifth is that concepts in models are inherently fuzzy. There is a prediction versus risk relation. And risk brings additional scrutiny and preparation challenges.
Data fusion technologies encompass a variety of characteristics. It is historically a deductively-based inferencing / estimation process. The resulting observations and estimates produce random variables optimized for minimum uncertainty. The process is adaptive in various ways. It enables observation management, process adaptation, and beneficial actions. Data fusion models can be used to analyze a broad set of areas. The physical domain is the easiest to accomplish fusion. This includes weapon systems and weather reports. The information domain is harder. This includes symbolic representation and interpretations of data and models. The cognitive domain includes beliefs, values, and emotions and is the most difficult to fuse.
Efforts are underway to create an automated multi-source, multi-sensor, multi-data fusion tool. One way they are doing this is by looking at textual information. They take documents of different types, use ABA tools and extract antecedents. The tools can grab information, bring it together, and end up with predictive models. Working toward multi-focused analysis, the tool must overcome the problem of sorting through tons of information.
Large Data Sets and Knowledge Extraction Techniques
Large data and visualization efforts are becoming an ever growing avalanche within the social science community. Loading all the data is hopeless. Therefore, efforts have focused on trying to load the structure of the data. This results in maximum expressiveness with minimum size. The structure of the data for documents includes terms, entities, and concepts. The structure for transaction, travel, and communication records include people, places, organizations, and relationships. However, smart loading still requires human guidance. A sandbox is an environment for “what if” questions and for constructing arguments. It should have quick access to exploratory tools and answer the question, “How are these actors connected?” The system’s job is to track workflow and allow for annotations and assumptions. The analyst can backtrack and replay, branch, and recombine. He may also retract or change assumptions. The output should embody a complete chain of reasoning.
Work is being undertaken to determine whether researchers could construct a scaffold for the data that can say something about the dataset. The geometry in the data set might help pull out information. By comparison if you look at physics, the math needed to model it is very tame math. In biology, the math needed is fundamentally different. Even though researchers have not discovered the laws of social science, there are some regularities, although they have not been captured in math to a sufficient depth.
The scale and speed of the data means that the classic, craftsman approach to machine learning is no longer possible. The answer is a commodity, hands-on model. This is a challenging task. Not only does commodity mean that researchers have to develop algorithms that are robust in the face of noise, skew, and the host of other ills; it also means that they have to work out how to set all algorithm parameters from the data or the context, so that the human analyst need not concern themselves with them. There is no single algorithmic magic bullet. There are lots of pattern recognition algorithms; some are well known, including decision trees, support vector machines, neural nets, nearest neighbors, naive Bayes. Ensembles are the first and the most powerful of the techniques to know about, as they permit you to squeeze all possible accuracy out of your data.
Overcoming Information Challenge in Federated Analysis: From Concepts to Practice.
Author | Editor: Canna, S. (NSI, Inc).
The Overcoming Information Challenge in Federated Analysis: from Concepts to Practice workshop, held on 27-28 August 2008, was convened in response to requests from US Special Operations Command and US Strategic Command, Lieutenant General Carter F. Ham, Director of Operations, J-3, Joint Staff. The workshop is part of an effort to develop national-level capability to identify and anticipate the action of Violent Non-State Actors (VNSA) with regard to their intent and capability to acquire, build, store, employ, deploy, or supply weapons of mass destruction (WMD). In support of this effort, the workshop was sponsored by a multiagency team and hosted at the Directed Technologies Incorporated (DTI) facility in Arlington, Virginia.
The purpose of the workshop was to identify analytical methods and tools that could (1) aid in the sorting of large volumes of unstructured, multilingual data and to (2) help make sense of the output. Concerted novel approaches to data trolling, ingest, characterization, processing, extraction, coding, and visualization may lead to great potential for proactive rather than reactive capabilities, not only within the military context, but within all components of national power.
Focusing on the front-end issues of the data analysis process will significantly improve our nation’s and its allies’ capabilities to proactively uncover global WMD proliferation. The workshop brought together a diverse group of physical and social scientists, academics, analysts, intelligence collection managers, operational planners, and decision makers to demonstrate and discuss usable techniques and methods for a more effective nexus of the federated informational and analytical processes.
This workshop examined technologies that could play a role in addressing the problems faced by the Strategic Multi-layer Analysis (SMA) team in marshalling data and putting it in a form that could be readily analyzed to perform quantitative analysis. The purpose of the workshop was to expose problems and offer potential solutions to the problem of ingesting large quantities of data, particularly data from multilingual text and coding it for use in analytical models. The discussion of the Weapons of Mass Destruction – Terrorism (WMD-T) Joint Intelligence Preparation of the Operational Environment (JIPOE) problem space and technical approach are included to give the reader an understanding of why the technologies being explored will be needed in the long term by any group seeking to look globally at non-state actors who may choose to use weapons of mass destruction.
JIPOE is a proven doctrinal process typically applied to a bounded geographic space.1 While it has rarely been applied to the government as a whole, the process can be used to assess the information challenge problem and the federated analysis solution. While the JIPOE process typically focuses on the commander, the process applies to any federal decision maker. The combined forces of the nature of globalization and increasing interdependency generated by the informational revolution have ushered in a new imperative for a more holistic understanding of the operation environment. This workshop addressed these issues and looked for solutions to automated multi-data lingual processing in a federated environment.
The objective of the WMD-T JIPOE effort is to develop a sustained, national-level means for combating WMD-Terrorism with a forecasting, anticipating, or inferential strategic environmental level assessment capability covering the full threat spectrum from intent to act, to acquisition and attack preparation, and all the way downstream to deployment by non-state actors (i.e., from far left to just left of “boom”). The ability of the government to process data, identify indicators of terrorism, and share those findings in a truly federate manner needs to be enhanced. As a consequence, the only way to fight a dynamic and adaptive threat network is a similarly dynamic and adaptive USG federated forecasting and anticipating assessment network.
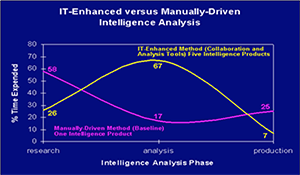
The notion of a sustained and repeatable capability requires that the adopted methods and processes be founded on robust scientific methods and theory. The nature of global reach forces the intelligence and defense communities to continue to enhance their efforts to exploit open source information and fuse it, as appropriate, with all the source information currently collected. The volume of that information demands that the effort use reliable automation technology to the fullest extent, recognizing that multilingual data mining is not mature for all languages. Even with the best data mining techniques, new methods for sorting the data and targeting the factors that will most reliably detect intent to acquire and use WMD must be established to avoid increasing the workload of already over-burdened analysts. Thus from the front end extraction processes to the back end analysis methods, existing tools must be augmented by emerging capabilities that keep analytical decisions properly centered on the human analysts while enhancing their performance.
Pieces of the WMD-T JIPOE capability already exist in various places among a number of groups within and outside the government. Thus the WMD-T JIPOE will work to take full advantage of these unique and disparate efforts in such a way that each participating group is capable of sustaining its own efforts while collaborating with and benefiting from the work of the other participants. The Information Challenge workshop highlighted pieces of the puzzle to join the research and the operation communities together to work toward a unified effort. The ultimate vision of the WMD-T JIPOE enterprise is a federation in which the WMD-T JIPOE cell is the core and integrator of data and where methods and tradecraft are shared among collaborating groups.
The workshop was designed to showcase tools and technologies that could be brought to bear on the information challenge problem. The problems and potential solutions explored in this workshop are common to challenges that rely on the ability to ingest large amounts of multilingual text information and extract from it data that can be used in analytical models.
Deterrence in the 21st Century: An Effects-Based Approach in an Interconnected World Volume II - Typologies.
Author | Editor: Chesser, N. (DTI).
This Deterrence Typology was created to assist in the development of deterrence options and plans for State and Non-State Actors. It can be used as a stand alone document for identifying important information to characterize and understand State or Non-State Actors. It can also assist in the development of initial questions that should be answered about either type of actor to be deterred.
This typology represents the merged product of three separate efforts to identify and categorize (a) the most relevant factors influencing the behavior and decisions of State and Non-State Actors and (b) the underlying elements of Decision Making by individuals and groups. Because it is the product of negotiation and consensus, some of the detail and richness of the descriptions developed specifically for State and Non-State Actors has been lost. However, the resulting merged product should be more valuable as a single resource for either type of Actors.
The section on Decision Making and the Decision Maker should help the user better understand which elements of the previous sections may be most influential in a specific scenario or situation and how they may impact the Decision Maker’s behavior. While the section on Decision Making Approaches may be one of the most important for understanding and affecting an Actor’s decision calculus, the information needed to make a determination about an approach may be difficult to ascertain without sufficient information about previous decisions made in a variety of situations and about the current context. Although a set of implications for each decision making style has been included to aid analysis and development of potential deterrence options, it is recommended that the user vet decision making approach determinations with appropriate subject matter experts.
This typology is organized into five (5) sub-typologies deemed relevant to describing the factors likely to impact an actor’s decision making process about a particular issue or action. The five sub-typologies are: Objectives, Motivation, Capabilities, Functional and Structural Environment (including the physical and human terrain), and Decision Making (see Table of Contents – next page). The overall format of the Deterrence Typology provides a brief definition of each sub- typology followed by a list of indicators of the sub-typology and observables. Suggested collection and analysis sources are enumerated under the observables.
The Deterrence Typology should be referred to for additional detail, definitions, and examples before and during completion of the Guiding Questions.
Collection & Analysis Caveats:
- Collection sources are representative versus exhaustive.
- “Analysis” implies the use of content analysis, pattern analysis (including nodal), trend analysis, change detection, and anomaly detection. Any additional factors are directly noted in the relevant section.
See the Annex for Information Sources and Methods

Deterrence in the 21st Century: An Effects-Based Approach in an Interconnected World Volume I
Author | Editor: Chesser, N. (DTI).
This report summarizes the results from a 120-day effort that was undertaken to meet these challenges. A scope of the effort is provided by Lt Col Shannahan in section 1; namely, decision makers, policy makers and commanders at all levels need to better understand deterrence theory applicable to the 21st century security environment. The USG requires a typology to understand the ways and means to deter a non-nation-state actor while simultaneously retaining the means to deter and compel nation-states.
The effort focused on the scientific underpinnings of deterrence. A broad viewpoint was adopted; namely actions that prevent an adversary from engaging in behaviors that threaten or oppose US national interests. For further elaborations please refer to the Glossary (Appendix B).
The effort, instead of focusing on an adversary’s capability as the basis for planning, refocuses analysis and planning on the actor’s motivations for action, his intent, and the structure of his decision problem as he sees it. Capability is not ignored, but actor’s perspective, motive and intent is at the core of this effort and the role of social science is paramount. The results are actualized in the Deterrence Analysis and Planning Support Environment (DAPSE) which is a web application that captures the depth of current academic thought along with established military doctrine to advise planners and associated staff with the means to deter the adversary. A DAPSE overview and description are provided in sections 2 and 3 by Dr Chesser and Stu Schwark & Altaf Bahora respectively.
A primary task of the Deterrence Strategic Multi-layer Analysis (SMA) project was developing a typology that could characterize the information needed for understanding adversaries and other actors of interest. A typology was developed that is consistent with various social science disciplines, and that incorporates a thorough consideration of human and cultural factors necessary for understanding what people value and how to influence them; i.e., a systems hierarchical paradigm for analyzing any society. The systems hierarchical approach is based on several anthropological ontologies that relate the various aspects of society, and is also based on inputs from the numerous social scientists involved in this project. Key aspects of a society captured in the systems hierarchical approach include ideology and religion, culturally based values, social organization, culturally prescribed roles, demography, and the actor’s decision making process, as well as capabilities.
These are described by Dr Larry Kuznar in section 4. While the DAPSE typology is one of the more complete and useful typologies for guiding analysis and planning, there are gaps. Two of the most obvious are a lack of consideration of language and history.
Drs Laurie Fenstermacher and Bob Popp discuss the role of modeling in section 5. Models, first and foremost, augment the ability of an analyst or planner, but do not in any way replace them. Models aren’t turnkey... they provide input to decisions, they don’t make them! They are good at producing a swath of forecasts (e.g., the range of probable locations for landfall of a hurricane), not good at producing point predictions (due to inherent uncertainty in the data or in the model itself). In addition, models can compensate for limits in subject matter expert (SME) knowledge. Due to the inherent complexity and dynamic nature of the systems and problems of interest, it is extremely difficult for an expert, or group of experts, to account for the effects of all possible interactions, particularly those with a low probability of occurrence. A complete reliance on SMEs will result in a very subjective assessment devoid of empirical evidence!
Section 6 by Dr Allison Astorino-Courtois outlines the use of the DAPSE Typology to guide the user’s information search and organization; “reconstruction” of the interest-based decision calculus from the deteree’s perspective; and techniques for analyzing that decision calculus to discover the most effective “influence levers” for deterring an opponent’s unacceptable activities. This is at the core of this deterrence effort and the reader is well advised to dwell on it.</p>, <p>Having identified the strategic context, deterrence objectives and decision calculus of actor(s) to be deterred, the analysis now turns to analyzing the truthfulness of the hypotheses (influence levers) emerging from the decision deterrent matrix, and also evaluating possible courses of action and their consequences under different conditions. These approaches are described in section 7 by Drs Bob Popp and Laurie Fenstermacher.
The final stage in the DAPSE process is a last check of the refined US deterrence option(s) identified and evaluated and tested. To do this the refined US deterrence option, now including actual US DIME (Diplomatic, Informational, Military, and Economic) actions, is “run” back through the Deterrence Decision Calculus (DDC) matrix. This is described in section 8 by Dr Allison Astorino-Courtois.
By now the reader should be aware that the approach taken focuses on the actor’s intent instead of focusing primarily on adversary capability...a necessary change after a near monopoly on capability fixation in the Cold War. This shift is the holy grail of the intel community and an essential maxim of our new world order – the shift from physical space to cognitive space. This necessitates the need to expand use of non-traditional sources of information and application of non-traditional analyses (e.g., cognitive and behavioral modeling). These are described in section 9 by Drs Bert Davis and Brian Meadows.
In section 10, LCDR Wes Latchford discusses perspectives on deterrence provided by the private sector. In support of the SMA, the GISC Partnership Group was asked to leverage its unique network of non-traditional domestic and international civilian business and academia experts to explore how particular elements of private sector enterprises approach the concept of "deterrence," the indicators utilized to determine when deterrence is necessary, and the "ways and means" by which deterrence is accomplished. The private sector provides a “Second Set of Eyes” perspective outside of DoD.
In section 11, Dr Carl Hunt and CAPT(S) Todd Veazie address the very important topic of networks and connections in developing a deterrence strategy. Their theme is that deterrence in the Cyber Age will not work as it did in the Cold War, simply because we will find it far more difficult to apply it and to understand feedback from its use – we may not be able to understand what the adversary values and thus never understand how to place that value at risk. This will absolutely require more consistent use of multi-disciplinary thinking and decision-making. We must create a Cyber Power-based DIME incorporating interconnectivity and economic interdependencies already emerging: we must change thinking about the DIME to include interconnectivity and shore up the economic, diplomatic and information components, while strengthening the potential of the military component.
Each of the sections in this report identifies, as appropriate, areas that need further work. In section 12, Dr Larry Kuznar identifies several key areas that clearly require more development. They include social neuroscience, global challenges, information age deterrence and strategic communication, and dynamism and complexity. Related to these is the potential for the development of a dynamic approach to deterrence that would incorporate feedback from on- going US COAs (courses of action) and re-evaluation of deterrence strategies, operations and tactics.
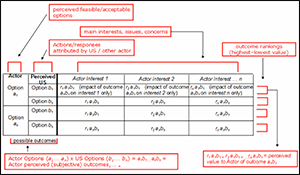
Having developed the methodology and a set of procedures, the effort turned next to several potential notional scenarios to assess whether or not they worked together to produce a viable result. In section 13, Dr Sue Numrich, explores one of the test scenarios in some depth. The scenario selected is based on a current problem – the influx of foreign fighters into Iraq. Although the DAPSE process is intended to be exercised over a longer time period, the analysts who developed this scenario worked over a period of only four days relying on their accumulated experience. The section summarizes a set of possible deterrence options based on this analysis.
Products resulting from efforts like this with heavy reliance on social science can atrophy rather fast. Col Tim Fay in section 14 discusses transition options being contemplated.
As the effort neared completion, the team applied the DAPSE to several NOTIONAL scenarios primarily to identify and rectify gaps/deficiencies. These are being published separately. The first three are classified and will be forwarded in appropriate channels:
- Scenario 1: Non-state
- Scenario 2: State – PACOM
- Scenario 3: State – CENTCOM
- Scenario 4: Sudan (multiple actors)
Many thanks are due to all who worked on this effort (see Appendix F), to the contributors to this report and finally to Dr. Nancy Chesser who patiently edited the report.

Authors: Dr. Sabrina Polansky (Pagano) (NSI, Inc.) and Tom Rieger . (NSI, Inc.)
Quick Look Preview
This report supported SMA’s Integrating Information in Joint Operations (IIJO) project. For additional speaker sessions and project publications, please visit the IIJO project page.
In the current environment of contested norms, increasing great power competition, and rapid technological change, protecting and furthering US interests requires the ability to compete effectively in the information environment (IE). In recent years, the IE has seen the proliferation of actors, channels of communication, and messages. To compete in this crowded and contested environment, we must be able to communicate effectively. Yet, the IE is complicated, available information is often vast and imperfect, time is constrained, and additionally, we are limited by our own cognitive capacity.
Humans have developed several adaptations to address these cognitive limitations, including heuristics and other mental shortcuts that facilitate survival by enabling more efficient processing of information from the environment. Unfortunately, these same shortcuts hardwire biases into our thinking and communication, which render messaging efforts ineffective and open to manipulation by adversaries seeking to mislead or confuse. These cognitive biases can lead to inaccurate judgments and poor decision- making that could trigger either unintended escalation or failures to identify threats in a timely manner. Understanding sources and types of cognitive bias can help minimize miscommunication and inform development of better strategies for responding to adversary attempts to leverage these biases to their advantage.
Author: Farwell, J. (King’s College, U. of London and Middle East Institute.)
Executive Summary
This report addresses the elements of narrative that lend coherence to US military activities that could help shape Chinese and Russian behaviors. From there, the paper looks at kinetic and non- kinetic tactics that are and will be used by competing powers domestically and abroad to undercut US interests over the coming decade. These responses do not factor in the potential impact of emerging technologies, including G5, Artificial Intelligence, and Quantum Computing. These seem likely to have a significant impact and the Pentagon would seem well advised to conduct new research that anticipates the scope and capacity of each technology and how each or all of them confluently affects tactics, strategies, and operations.
This essay focuses on tactics, not the broader questions of operations or strategy as the United States wrestles with the implications of New Generation Warfare (NGW). Russia’s term is “hybrid warfare.” China’s approach is expressed in its Three Warfares concept. The West talks about “Gray Zone” warfare.
NGW is usually discussed in military circles. But it is more distinctly a political notion, not a military one, although its strategies incorporate military aspects and, especially for Russia, kinetic activity. All three nations’ notions think of NGW as action short of warfare.
The Russian notion of hybrid warfare emanates from the “active measures” employed by Russian intelligence during the Cold War and preceding it. Its approach seeks to create disruption, chaos, fear, uncertainty, and loss of confidence in the media as well as in public and private institutions. The approach includes weaponized social media, coercion, bribery, disinformation, intimidation, and unattributed kinetic action.
The Chinese notion is more sophisticated and builds upon a late 1990s concept of combination warfare that was adapted from its perception of US approaches, based on observations about how the United States operated during Desert Storm in Iraq. China has evolved its approach into a “Three Warfares” concept that confluently employs lawfare, psychological warfare, and media warfare. China leverages the state’s authoritarian power to integrate its concept with diplomatic, intelligence, and economic strategies such as the Belt and Road Initiative. China is vigorously promoting its version of 5G for the Internet, tying it to Huawei, and requiring users to employ Chinese standards and technology. It has been well observed that China’s “aid” turns nations into debtor states, could hamper free trade, and “could set global and regulatory and technical standards for new technology that could provide advantages to Chinese companies over others.” Its use of media warfare and other tactics helps present Chinese actions in a deceptive light that the United States and its partners should expose, discredit, and de-legitimize.
This report proceeds to examine the Russian hybrid warfare and the Chinese Three Warfare concepts in depth. It suggests elements both of a US and a multilateral allied narrative that could lend coherence to US military activities and could help shape Chinese and Russian behaviors in a manner that better serves US national interests. Understanding how to address their concepts and forging new strategies and tactics that leverage our unique strengths to gain a competitive edge is vital to our current and future security.
Author | Editor: Kuznar, E. (NSI, Inc.)
Executive Summary
Data
Two datasets on wealth and income distribution were analyzed for Croatia’s country report: the 2017 World Bank quintile and decile estimates of income and data collected by Croatia’s government that provides the mean monthly income and number of employees for specific occupations.
Results
Croatia’s Arrow-Pratt score is one of the lowest scores in this study, ranking it 151 of 158. Its low Arrow- Pratt score indicates that Croatia’s population is highly risk acceptant. This risk acceptance is constant across both datasets, with those who earn the highest incomes scoring as the most risk acceptant.
Implications for US Interests
Croatia is strategically valuable to the US and other Western countries due to the role it plays in the Balkans. Its acceptance into the European Union during 2013 gave the US and its allies in NATO and the EU an important ally that can be used to confront Russian encroachment into the region and help other former Yugoslavian states democratize and potentially join the EU. Croatia’s highly risk acceptant population poses a risk to the US and its Western allies in the EU that rely upon its political stability to lead other Balkan nations away from Russia and toward a more democratic state.
Implications for China’s Interests
China has been increasing its bilateral trade with Croatia in order to curry favor and further its Belt and Road Initiative (BRI), which Beijing has designed to flow through the Balkans and continue further into Europe. However, Croatia’s membership in the EU creates roadblocks for pursuing deeper economic or political interests in Croatia. The Croatian population’s risk acceptance provides Beijing the potential to influence Croatia through its BRI, if China can demonstrate how its increased influence will translate to socioeconomic opportunities for a population seemingly eager to take risks on new partners and opportunities.
Implications for Russia’s Interests
Croatia stands as a roadblock to Russia’s influence in the region. As a result, Russia only has minor economic investments in Croatia. It is plausible that Croatia is a larger threat to Russia’s aspirations in the Balkans more than ever before as Croatia has achieved both EU membership and has pledged to bring other Balkan states into the EU. Croatia and Russia’s somewhat confrontational relationship gives Russia little opportunity to increase its influence in the country even with Croatia’s risk acceptant nature. However, the ability to disseminate Russian propaganda and political influence is still possible for Moscow as in recent years Croatia has narrowly dodged political crisis after a 2016 vote of no confidence in its Prime Minister (Skrpec, 2017).
Author(s): Astorino-Courtois, A. (NSI); Cooley, S. (Oklahoma State University); Dorondo, D. (Western Carolina University); Elder, R. (George Mason University); Kuznar, L. (NSI); Olsher, D. (Integral Mind); Popp, G. (NSI); Sleevi, N. (TRADOC); Suedfeld, P. (University of British Columbia); Wright, N. (Intelligent Biology)
Report Preview
Over the course of this project, multiple sets of questions were edited and added to the effort, resulting in a total of 29 questions. In this document, the individual teams have addressed as many of the questions in this list as addressed by their research and analytic efforts for this SMA project.
The list of 29 questions is divided into five sections throughout this report.
Section I: Regional Analyses includes questions examining the ins-and-outs, implications, and potential outcomes from a regional perspective. These questions investigate: key actor interests, the interplay of conceivable actions by these actors, conditions that would support or lead to potential outcomes. Many of the SMA teams were able to apply their individual methodologies or tools to address these questions. The modeling teams included TRADOC’s ATHENA, GMU’s Timed Influence Net (TIN) modeling, and Integral Mind’s cognitive simulation. The analytic approaches included: NSI’s I-R-C Analysis and Pathways Analysis, UBC’s Integrative Complexity, Intelligent Biology’s Cognitive Assessment, NSI’s Quantitative Discourse Analysis, and OSU’s Strategic Media Messaging Analysis. Finally, the SMA teams incorporated subject matter expert via NSI’s ViTTa effort and analysis from an expert from Western Carolina University.
Questions from Section II: DPRK Analyses focus internally on the stability of the DPRK state and economy. DPRK state stability are explored by modeling teams of ATHENA and Integral Mind modeling teams alongside the NSI analytic and ViTTa approaches.
In Section III: Proliferation v. Denuclearization, the I-R-C and ViTTa analyses thoroughly review conditions and options for denuclearization while the OSU team examines the messaging narratives from Russian and Chinese media. Three SMA teams, Intelligent Biology, UBC, and Integral Mind, take a cognitive approach to examining the way towards denuclearization.
Section IV: Regional Objectives, Actions & Implications covers future outcomes and explores the implications of regional actions. In this section, the modeling efforts by GMU and TRADOC submit future scenarios and examine the steps taken to get there. Two ViTTa analyses and work by the cognitive assessment and discourse teams address how the US can work with partners in the region.
In Section V: Cognitive Assessment of KJU Confidence, Cognition, and Discourse, four SMA teams shared a common corpus and conducted seven different analyses: quantitative discourse analysis, cognitive mapping, thematic content analysis, integrative cognitive complexity analysis and motive imagery scoring, application of the empathy checklist, basic emotive analysis, and discourse of deception. From these initial analyses, the teams went on to address questions of KJU’s regime confidence and assurance, and recommended communication strategies that would appeal to KJU’s communication styles and cognitive proclivities. For more in-depth reading, please refer to the full reports submitted by the individual teams. Links to these reports can be found in the appendix. Review the Part I report for a summation of the key findings across all of the individual efforts.
Authors: Dr. Sara Kitsch (Monmouth College); Dr. Skye Cooley (Oklahoma State University); Dr. Robert Hinck (Monmouth College); Dr. Asya Cooley (Oklahoma State University)
Quick Look Preview
Overview
This report supported SMA’s Integrating Information in Joint Operations (IIJO) project. For additional speaker sessions and project publications, please visit the IIJO project page.
This Quick Look specifically assesses and describes how one area of social scientific research, called Inoculation Theory, can be used to build individual resistance to attitude change, especially as it relates to force protection against misinformation, fake news, and conspiracy theories. An essential part of understanding how individuals are persuaded to change their attitudes involves understanding how they resist persuasion and attitude change (Banas & Rains, 2010). Inoculation Theory has continued to receive scholarly support and attention for the past two decades. As the name suggests, inoculation to persuasion operates in basically the same way as medical inoculation (Compton, 2013). When you get a flu shot, a weakened form of the virus is injected into you, enabling your body to build up resistance to future attacks from the virus (Banas & Rains, 2010). Similarly, Inoculation Theory maintains that when individuals are exposed to weakened versions of arguments against attitudes they currently hold, they are able to build up resistance and counterarguments to future threats to those attitudes.
Applications of Inoculation Theory have been made to health, politics, and commerce (Compton, 2013). We can also see, and recent research supports, how Inoculation Theory can be applied to help solve pressing twenty-first century issues related to information spread, propaganda, and source credibility. Recent studies, which will be explored in this report, focus on how we can potentially “vaccinate” citizens against misinformation, fake news, and conspiracy theories. This report begins with a summary of the original conceptualization of Inoculation Theory, followed by updates and advancements designed to address early conceptual and data limitations, and ends with a summary of current research, including practical applications (Banas & Miller, 2013).